[ad_1]
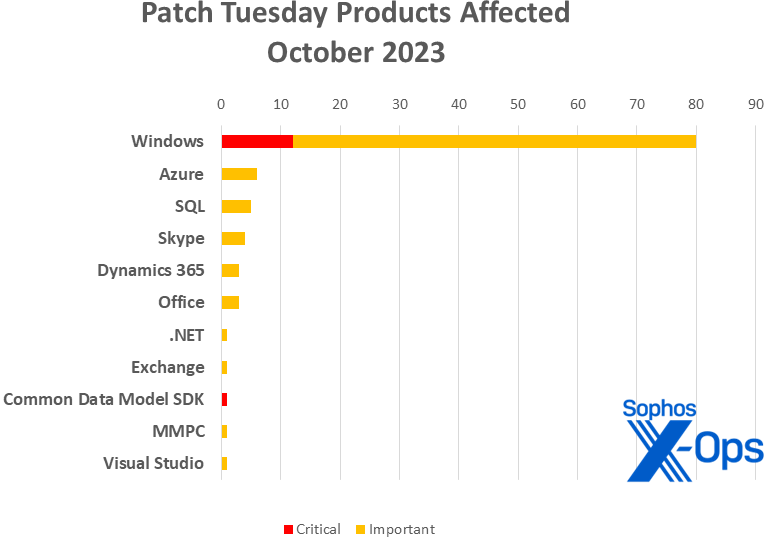
Microsoft on Tuesday launched patches for 104 vulnerabilities, together with 80 for Home windows. Ten different product teams are additionally affected. Of the 104 CVEs addressed, 11 are thought of Important in severity; ten of these are in Home windows, whereas one falls within the Microsoft Frequent Knowledge Mannequin SDK. (The Frequent Knowledge Mannequin is a metadata system for business-related information.) One CVE, an Necessary-severity denial-of-service problem (CVE-2023-38171), impacts not solely Home windows however each .NET and Visible Studio.
At patch time, two points involving WordPad and Skype are identified to be below exploit within the wild. A further 10 vulnerabilities in Home windows, Alternate, and Skype are by the corporate’s estimation extra prone to be exploited within the subsequent 30 days. For ease of prioritization, these 12 points are:
| Product household | CVE | Energetic exploitation | Advice |
| Skype | CVE-2023-41763 | Detected within the wild | Patch instantly |
| Home windows (WordPad) | CVE-2023-36563 | Detected within the wild | Patch instantly |
| Alternate | CVE-2023-36778 | Doubtless with 30 days | Patch ASAP |
| Skype | CVE-2023-36780 | Doubtless with 30 days | Patch ASAP |
| Home windows | CVE-2023-36594 | Doubtless with 30 days | Patch ASAP |
| Home windows | CVE-2023-36713 | Doubtless with 30 days | Patch ASAP |
| Home windows | CVE-2023-36731 | Doubtless with 30 days | Patch ASAP |
| Home windows | CVE-2023-36732 | Doubtless with 30 days | Patch ASAP |
| Home windows | CVE-2023-36743 | Doubtless with 30 days | Patch ASAP |
| Home windows | CVE-2023-36776 | Doubtless with 30 days | Patch ASAP |
| Home windows | CVE-2023-38159 | Doubtless with 30 days | Patch ASAP |
| Home windows | CVE-2023-41772 | Doubtless with 30 days | Patch ASAP |
Some of the fascinating gadgets on this month’s launch isn’t even a patch – although to be honest, it’s not a difficulty that may be “patched” within the typical sense, for Microsoft merchandise or many others. CVE-2023-44487, an Necessary-severity denial of service problem, describes a rapid-reset assault in opposition to HTTP/2, at the moment below extraordinarily energetic exploit within the wild. It carries a MITRE-assigned CVE quantity (a rarity; often Microsoft assigns its personal CVEs numbers) and, in line with Microsoft’s finder-acknowledgement system, is “credited” to Google, Amazon, and Cloudflare. The record of affected product households is lengthy: .NET, ASP.NET, Visible Studio, and varied iterations of Home windows. Microsoft has printed an article on the matter. It’s not included within the patch tallies on this put up, although the article states that the corporate is releasing mitigations – not patches, mitigation — for IIS, .NET, and Home windows. There’s a really useful workaround, although – going into RegEdit and disabling the HTTP/2 protocol in your internet server. Google has posted a superb rationalization of this assault.
Past Patch Tuesday, the keepers of curl (the open-source command-line device) additionally had a big patch on faucet for Wednesday, 11 October. In accordance with the advisory posted to GitHub, CVE-2023-38545 and CVE-2023-38546 each describe points in libcurl, with CVE-2023-38545, a heap-overflow problem, additionally touching curl itself. These are critical enterprise; in line with Daniel Stenberg, the maintainer who wrote the GitHub advisory, “[CVE-2023-38545] might be the worst curl safety flaw in a very long time.” Since curl lies on the coronary heart of such in style protocols as SSL, TLS, HTTP, and FTP, system directors are suggested within the strongest doable phrases to familiarize themselves with the brand new curl 8.4.0 launch, which addresses this problem.
October can be a giant month for goodbyes. The tables in Appendix E on the finish of this text record the Microsoft merchandise reaching end-of-servicing (lined below the Fashionable Coverage) and finish of assist (lined below the Mounted Coverage) right now, in addition to these transferring from Mainstream to Prolonged assist. Prolonged assist consists of free safety updates, however no extra new options or design adjustments. The record of merchandise affected is lengthy and thrilling – specifically, Workplace 2019 not taking characteristic updates is a milestone – however the headline act on this month’s cruise into the sundown is unquestionably Server 2012 and Server 2012R2. As a going-away current, that venerable model of the platform receives 65 patches, 11 of them critical-severity, one below energetic exploit within the wild.
We’re as typical together with on the finish of this put up three appendices itemizing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product household. As per Microsoft’s steerage we’ll deal with the Chromium patch as information-only and never embody it within the following charts and totals, although we’ve added a chart on the finish of the put up offering fundamental info on that. (CVE-2023-44487, mentioned above, additionally applies to Chromium; that is additionally famous within the appendix.)
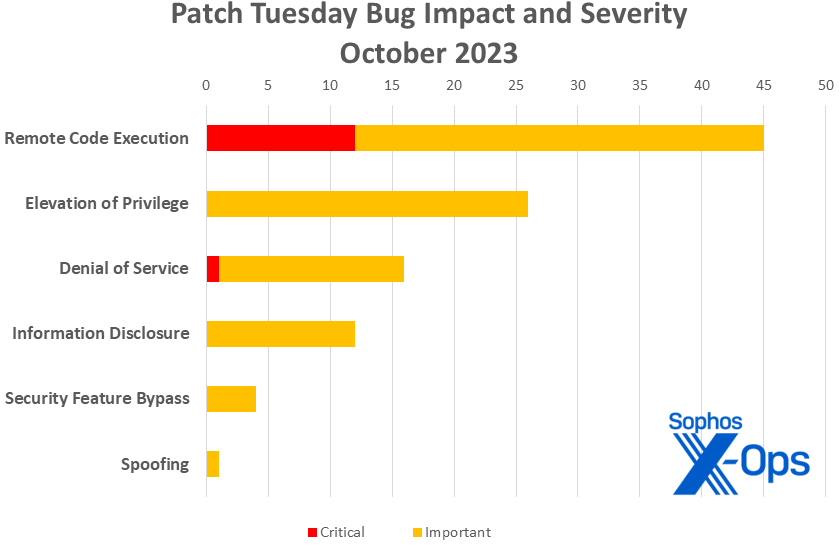
- Complete Microsoft CVEs: 2
- Complete advisories delivery in replace: 2
- Publicly disclosed: 2
- Exploited: 2
- Severity
- Important: 13
- Necessary: 91
- Influence
- Distant Code Execution: 45
- Elevation of Privilege: 26
- Denial of Service: 16
- Data Disclosure: 12
- Safety Characteristic Bypass: 4
- Spoofing: 1
Determine 1: October is a heavy patch month with somewhat little bit of every part
Merchandise
- Home windows: 80 (together with one shared with .NET and Visible Studio)
- Azure: 6
- SQL: 5
- Skype: 4
- Dynamics 365: 3
- Workplace: 3
- .NET: 1 (shared with Visible Studio and Home windows)
- Alternate: 1
- Microsoft Frequent Knowledge Mannequin SDK: 1
- MMPC: 1
- Visible Studio: 1 (shared with .NET and Home windows)
Determine 2: Merchandise affected by October’s patches. For gadgets that apply to a couple of product household (e.g., the patch shared by Home windows, Visible Studio, and .NET), the chart represents these patches in every household to which they apply, making the workload look barely heavier than it will likely be in apply
Notable October updates
Along with the high-priority points mentioned above, a number of fascinating gadgets current themselves.
9 CVEs — Layer 2 Tunneling Protocol Distant Code Execution Vulnerability
5 CVEs — Win32k Elevation of Privilege Vulnerability
Identically named CVEs are hardly uncommon in these releases; this month additionally has identically named units of 16 (Microsoft Message Queuing Distant Code Execution Vulnerability), 4 (Microsoft Message Queuing Denial of Service Vulnerability), and three (too many to record) CVEs. Nevertheless, the 9 RCEs touching Home windows’ Layer 2 tunnelling protocol additionally share Important-severity standing (CVSS 3.1 base is 8.1) and are thus value taking a look at sooner relatively than later. Thankfully, Microsoft doesn’t consider any of them to be extra prone to be exploited within the subsequent 30 days. The 5 EoP points touching Win32K, then again, are all thought of extra prone to see exploitation within the subsequent 30 days.
CVE-2023-36563 — Microsoft WordPad Data Disclosure Vulnerability
That is as talked about one of many two vulnerabilities below energetic exploit within the wild; Microsoft states that Preview Pane is a vector.
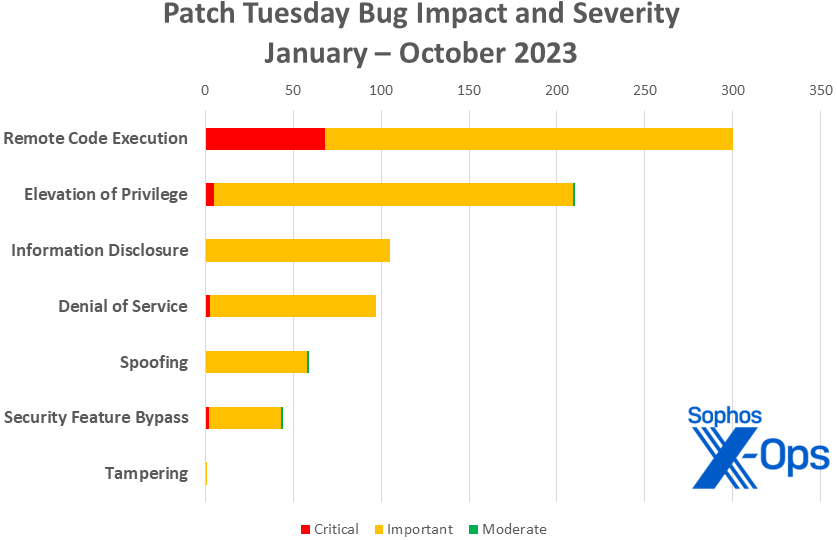
Determine 3: With two months to go in 2023, Microsoft has issued precisely 300 patches in opposition to distant code execution problem, probably the most of any class of vulnerability this yr
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2023-36594 | Exp/2336594-A | Exp/2336594-A |
| CVE-2023-36713 | Exp/2336713-A | Exp/2336713-A |
| CVE-2023-36731 | Exp/2336731-A | Exp/2336731-A |
| CVE-2023-36743 | Exp/2336743-A | Exp/2336743-A |
| CVE-2023-36776 | Exp/2336776-A | Exp/2336776-A |
| CVE-2023-38159 | Exp/2338159-A | Exp/2338159-A |
| CVE-2023-41772 | Exp/2341772-A | Exp/2341772-A |
As you may each month, in the event you don’t need to wait to your system to drag down Microsoft’s updates itself, you may obtain them manually from the Home windows Replace Catalog web site. Run the winver.exe device to find out which construct of Home windows 10 or 11 you’re working, then obtain the Cumulative Replace package deal to your particular system’s structure and construct quantity.
With regard to CVE-2023-44487, the best choice for thwarting the denial-of-service assault enabled by the vulnerability is to observe Microsoft’s printed recommendation.
Appendix A: Vulnerability Influence and Severity
This can be a record of October’s patches sorted by impression, then sub-sorted by severity. Every record is additional organized by CVE.
Distant Code Execution (45 CVEs)
| Important severity | |
| CVE-2023-35349 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36697 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36718 | Home windows Digital Trusted Platform Module Elevation of Privilege Vulnerability |
| CVE-2023-38166 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41765 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41767 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41768 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41769 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41770 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41771 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41773 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41774 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2023-36414 | Azure Identification SDK Distant Code Execution Vulnerability |
| CVE-2023-36415 | Azure Identification SDK Distant Code Execution Vulnerability |
| CVE-2023-36417 | Microsoft SQL OLE DB Distant Code Execution Vulnerability |
| CVE-2023-36418 | Azure RTOS GUIX Studio Distant Code Execution Vulnerability |
| CVE-2023-36420 | Microsoft ODBC Driver for SQL Server Distant Code Execution Vulnerability |
| CVE-2023-36436 | Home windows MSHTML Platform Distant Code Execution Vulnerability |
| CVE-2023-36557 | PrintHTML API Distant Code Execution Vulnerability |
| CVE-2023-36570 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36571 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36572 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36573 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36574 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36575 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36577 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2023-36578 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36582 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36583 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36589 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36590 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36591 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36592 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36593 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36598 | Microsoft WDAC ODBC Driver Distant Code Execution Vulnerability |
| CVE-2023-36702 | Microsoft DirectMusic Distant Code Execution Vulnerability |
| CVE-2023-36704 | Home windows Setup Recordsdata Cleanup Distant Code Execution Vulnerability |
| CVE-2023-36710 | Home windows Media Basis Core Distant Code Execution Vulnerability |
| CVE-2023-36730 | Microsoft ODBC Driver for SQL Server Distant Code Execution Vulnerability |
| CVE-2023-36778 | Microsoft Alternate Server Distant Code Execution Vulnerability |
| CVE-2023-36780 | Skype for Enterprise Distant Code Execution Vulnerability |
| CVE-2023-36785 | Microsoft ODBC Driver for SQL Server Distant Code Execution Vulnerability |
| CVE-2023-36786 | Skype for Enterprise Distant Code Execution Vulnerability |
| CVE-2023-36789 | Skype for Enterprise Distant Code Execution Vulnerability |
| CVE-2023-36902 | Home windows Runtime Distant Code Execution Vulnerability |
Elevation of Privilege (26 CVEs)
| Necessary severity | |
| CVE-2023-36419 | Azure HDInsight Apache Oozie Workflow Scheduler Elevation of Privilege Vulnerability |
| CVE-2023-36434 | Home windows IIS Server Elevation of Privilege Vulnerability |
| CVE-2023-36561 | Azure DevOps Server Elevation of Privilege Vulnerability |
| CVE-2023-36565 | Microsoft Workplace Graphics Elevation of Privilege Vulnerability |
| CVE-2023-36568 | Microsoft Workplace Click on-To-Run Elevation of Privilege Vulnerability |
| CVE-2023-36569 | Microsoft Workplace Elevation of Privilege Vulnerability |
| CVE-2023-36594 | Home windows Graphics Part Elevation of Privilege Vulnerability |
| CVE-2023-36605 | Home windows Named Pipe Filesystem Elevation of Privilege Vulnerability |
| CVE-2023-36701 | Microsoft Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2023-36711 | Home windows Runtime C++ Template Library Elevation of Privilege Vulnerability |
| CVE-2023-36712 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-36721 | Home windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2023-36723 | Home windows Container Supervisor Service Elevation of Privilege Vulnerability |
| CVE-2023-36725 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-36726 | Home windows Web Key Alternate (IKE) Extension Elevation of Privilege Vulnerability |
| CVE-2023-36729 | Named Pipe File System Elevation of Privilege Vulnerability |
| CVE-2023-36731 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36732 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36737 | Azure Community Watcher VM Agent Elevation of Privilege Vulnerability |
| CVE-2023-36743 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36776 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36790 | Home windows RDP Encoder Mirror Driver Elevation of Privilege Vulnerability |
| CVE-2023-38159 | Home windows Graphics Part Elevation of Privilege Vulnerability |
| CVE-2023-41763 | Skype for Enterprise Elevation of Privilege Vulnerability |
| CVE-2023-41766 | Home windows Consumer Server Run-time Subsystem (CSRSS) Elevation of Privilege Vulnerability |
| CVE-2023-41772 | Win32k Elevation of Privilege Vulnerability |
Denial of Service (16 CVEs)
| Important severity | |
| CVE-2023-36566 | Microsoft Frequent Knowledge Mannequin SDK Denial of Service Vulnerability |
| Necessary severity | |
| CVE-2023-36431 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36435 | Microsoft QUIC Denial of Service Vulnerability |
| CVE-2023-36579 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36581 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36585 | Energetic Template Library Denial of Service Vulnerability |
| CVE-2023-36602 | Home windows TCP/IP Denial of Service Vulnerability |
| CVE-2023-36603 | Home windows TCP/IP Denial of Service Vulnerability |
| CVE-2023-36606 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36703 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2023-36707 | Home windows Deployment Providers Denial of Service Vulnerability |
| CVE-2023-36709 | Microsoft AllJoyn API Denial of Service Vulnerability |
| CVE-2023-36717 | Home windows Digital Trusted Platform Module Denial of Service Vulnerability |
| CVE-2023-36720 | Home windows Combined Actuality Developer Instruments Denial of Service Vulnerability |
| CVE-2023-36728 | Microsoft SQL Server Denial of Service Vulnerability |
| CVE-2023-38171 | Microsoft QUIC Denial of Service Vulnerability |
Data Disclosure (12 CVEs)
| Necessary severity | |
| CVE-2023-29348 | Home windows Distant Desktop Gateway (RD Gateway) Data Disclosure Vulnerability |
| CVE-2023-36429 | Microsoft Dynamics 365 Data Disclosure Vulnerability |
| CVE-2023-36433 | Microsoft Dynamics 365 (On-Premises) Data Disclosure Vulnerability |
| CVE-2023-36438 | Home windows TCP/IP Data Disclosure Vulnerability |
| CVE-2023-36563 | Microsoft WordPad Data Disclosure Vulnerability |
| CVE-2023-36567 | Home windows Deployment Providers Data Disclosure Vulnerability |
| CVE-2023-36576 | Home windows Kernel Data Disclosure Vulnerability |
| CVE-2023-36596 | Distant Process Name Data Disclosure Vulnerability |
| CVE-2023-36706 | Home windows Deployment Providers Data Disclosure Vulnerability |
| CVE-2023-36713 | Home windows Frequent Log File System Driver Data Disclosure Vulnerability |
| CVE-2023-36722 | Energetic Listing Area Providers Data Disclosure Vulnerability |
| CVE-2023-36724 | Home windows Energy Administration Service Data Disclosure Vulnerability |
Safety Characteristic Bypass (4 CVEs)
| Necessary severity | |
| CVE-2023-36564 | Home windows Search Safety Characteristic Bypass Vulnerability |
| CVE-2023-36584 | Home windows Mark of the Net Safety Characteristic Bypass Vulnerability |
| CVE-2023-36698 | Home windows Kernel Safety Characteristic Bypass Vulnerability |
| CVE-2023-36700 | Microsoft Defender Safety Characteristic Bypass Vulnerability |
Spoofing (1 CVE)
| Necessary severity | |
| CVE-2023-36416 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
Appendix B: Exploitability
This can be a record of the October CVEs judged by Microsoft to be extra prone to be exploited within the wild inside the first 30 days post-release, in addition to these already identified to be below exploit. Every record is additional organized by CVE.
| Exploitation detected | |
| CVE-2023-36563 | Microsoft WordPad Data Disclosure Vulnerability |
| CVE-2023-41763 | Skype for Enterprise Elevation of Privilege Vulnerability |
| Exploitation extra probably | |
| CVE-2023-36594 | Home windows Graphics Part Elevation of Privilege Vulnerability |
| CVE-2023-36713 | Home windows Frequent Log File System Driver Data Disclosure Vulnerability |
| CVE-2023-36731 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36732 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36743 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36776 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36778 | Microsoft Alternate Server Distant Code Execution Vulnerability |
| CVE-2023-36780 | Skype for Enterprise Distant Code Execution Vulnerability |
| CVE-2023-38159 | Home windows Graphics Part Elevation of Privilege Vulnerability |
| CVE-2023-41772 | Win32k Elevation of Privilege Vulnerability |
Appendix C: Merchandise Affected
This can be a record of October’s patches sorted by product household, then sub-sorted by severity. Every record is additional organized by CVE.
Home windows (80 CVEs)
| Important severity | |
| CVE-2023-35349 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36697 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36718 | Home windows Digital Trusted Platform Module Elevation of Privilege Vulnerability |
| CVE-2023-38166 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41765 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41767 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41768 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41769 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41770 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41771 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41773 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| CVE-2023-41774 | Layer 2 Tunneling Protocol Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2023-29348 | Home windows Distant Desktop Gateway (RD Gateway) Data Disclosure Vulnerability |
| CVE-2023-36431 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36434 | Home windows IIS Server Elevation of Privilege Vulnerability |
| CVE-2023-36435 | Microsoft QUIC Denial of Service Vulnerability |
| CVE-2023-36436 | Home windows MSHTML Platform Distant Code Execution Vulnerability |
| CVE-2023-36438 | Home windows TCP/IP Data Disclosure Vulnerability |
| CVE-2023-36557 | PrintHTML API Distant Code Execution Vulnerability |
| CVE-2023-36563 | Microsoft WordPad Data Disclosure Vulnerability |
| CVE-2023-36564 | Home windows Search Safety Characteristic Bypass Vulnerability |
| CVE-2023-36567 | Home windows Deployment Providers Data Disclosure Vulnerability |
| CVE-2023-36570 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36571 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36572 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36573 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36574 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36575 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36576 | Home windows Kernel Data Disclosure Vulnerability |
| CVE-2023-36577 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2023-36578 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36579 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36581 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36582 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36583 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36584 | Home windows Mark of the Net Safety Characteristic Bypass Vulnerability |
| CVE-2023-36585 | Energetic Template Library Denial of Service Vulnerability |
| CVE-2023-36589 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36590 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36591 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36592 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36593 | Microsoft Message Queuing Distant Code Execution Vulnerability |
| CVE-2023-36594 | Home windows Graphics Part Elevation of Privilege Vulnerability |
| CVE-2023-36596 | Distant Process Name Data Disclosure Vulnerability |
| CVE-2023-36598 | Microsoft WDAC ODBC Driver Distant Code Execution Vulnerability |
| CVE-2023-36602 | Home windows TCP/IP Denial of Service Vulnerability |
| CVE-2023-36603 | Home windows TCP/IP Denial of Service Vulnerability |
| CVE-2023-36605 | Home windows Named Pipe Filesystem Elevation of Privilege Vulnerability |
| CVE-2023-36606 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36698 | Home windows Kernel Safety Characteristic Bypass Vulnerability |
| CVE-2023-36701 | Microsoft Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2023-36702 | Microsoft DirectMusic Distant Code Execution Vulnerability |
| CVE-2023-36703 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2023-36704 | Home windows Setup Recordsdata Cleanup Distant Code Execution Vulnerability |
| CVE-2023-36706 | Home windows Deployment Providers Data Disclosure Vulnerability |
| CVE-2023-36707 | Home windows Deployment Providers Denial of Service Vulnerability |
| CVE-2023-36709 | Microsoft AllJoyn API Denial of Service Vulnerability |
| CVE-2023-36710 | Home windows Media Basis Core Distant Code Execution Vulnerability |
| CVE-2023-36711 | Home windows Runtime C++ Template Library Elevation of Privilege Vulnerability |
| CVE-2023-36712 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-36713 | Home windows Frequent Log File System Driver Data Disclosure Vulnerability |
| CVE-2023-36717 | Home windows Digital Trusted Platform Module Denial of Service Vulnerability |
| CVE-2023-36720 | Home windows Combined Actuality Developer Instruments Denial of Service Vulnerability |
| CVE-2023-36721 | Home windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2023-36722 | Energetic Listing Area Providers Data Disclosure Vulnerability |
| CVE-2023-36723 | Home windows Container Supervisor Service Elevation of Privilege Vulnerability |
| CVE-2023-36724 | Home windows Energy Administration Service Data Disclosure Vulnerability |
| CVE-2023-36725 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-36726 | Home windows Web Key Alternate (IKE) Extension Elevation of Privilege Vulnerability |
| CVE-2023-36729 | Named Pipe File System Elevation of Privilege Vulnerability |
| CVE-2023-36731 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36732 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36743 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36776 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36790 | Home windows RDP Encoder Mirror Driver Elevation of Privilege Vulnerability |
| CVE-2023-36902 | Home windows Runtime Distant Code Execution Vulnerability |
| CVE-2023-38159 | Home windows Graphics Part Elevation of Privilege Vulnerability |
| CVE-2023-38171 | Microsoft QUIC Denial of Service Vulnerability |
| CVE-2023-41766 | Home windows Consumer Server Run-time Subsystem (CSRSS) Elevation of Privilege Vulnerability |
| CVE-2023-41772 | Win32k Elevation of Privilege Vulnerability |
Azure (6 CVEs)
| Necessary severity | |
| CVE-2023-36414 | Azure Identification SDK Distant Code Execution Vulnerability |
| CVE-2023-36415 | Azure Identification SDK Distant Code Execution Vulnerability |
| CVE-2023-36418 | Azure RTOS GUIX Studio Distant Code Execution Vulnerability |
| CVE-2023-36419 | Azure HDInsight Apache Oozie Workflow Scheduler Elevation of Privilege Vulnerability |
| CVE-2023-36561 | Azure DevOps Server Elevation of Privilege Vulnerability |
| CVE-2023-36737 | Azure Community Watcher VM Agent Elevation of Privilege Vulnerability |
SQL (5 CVEs)
| Necessary severity | |
| CVE-2023-36417 | Microsoft SQL OLE DB Distant Code Execution Vulnerability |
| CVE-2023-36420 | Microsoft ODBC Driver for SQL Server Distant Code Execution Vulnerability |
| CVE-2023-36728 | Microsoft SQL Server Denial of Service Vulnerability |
| CVE-2023-36730 | Microsoft ODBC Driver for SQL Server Distant Code Execution Vulnerability |
| CVE-2023-36785 | Microsoft ODBC Driver for SQL Server Distant Code Execution Vulnerability |
Skype (4 CVEs)
| Necessary severity | |
| CVE-2023-36780 | Skype for Enterprise Distant Code Execution Vulnerability |
| CVE-2023-36786 | Skype for Enterprise Distant Code Execution Vulnerability |
| CVE-2023-36789 | Skype for Enterprise Distant Code Execution Vulnerability |
| CVE-2023-41763 | Skype for Enterprise Elevation of Privilege Vulnerability |
Dynamics 365 (3 CVEs)
| Necessary severity | |
| CVE-2023-36416 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2023-36429 | Microsoft Dynamics 365 Data Disclosure Vulnerability |
| CVE-2023-36433 | Microsoft Dynamics 365 (On-Premises) Data Disclosure Vulnerability |
Workplace (3 CVEs)
| Necessary severity | |
| CVE-2023-36565 | Microsoft Workplace Graphics Elevation of Privilege Vulnerability |
| CVE-2023-36568 | Microsoft Workplace Click on-To-Run Elevation of Privilege Vulnerability |
| CVE-2023-36569 | Microsoft Workplace Elevation of Privilege Vulnerability |
.NET (1 CVE)
| Necessary severity | |
| CVE-2023-38171 | Microsoft QUIC Denial of Service Vulnerability |
Alternate (1 CVE)
| Necessary severity | |
| CVE-2023-36778 | Microsoft Alternate Server Distant Code Execution Vulnerability |
Microsoft Frequent Knowledge Mannequin SDK (1 CVE)
| Important severity | |
| CVE-2023-36566 | Microsoft Frequent Knowledge Mannequin SDK Denial of Service Vulnerability |
MMPC (1 CVE)
| Necessary severity | |
| CVE-2023-36700 | Microsoft Defender Safety Characteristic Bypass Vulnerability |
Visible Studio (1 CVE)
| Necessary severity | |
| CVE-2023-38171 | Microsoft QUIC Denial of Service Vulnerability |
Appendix D: Different Merchandise
This can be a record of advisories within the October Microsoft launch, sorted by product group.
Chromium / Edge (1 problem)
| CVE-2023-5346 | Chromium: CVE-2023-5346 Sort Confusion in V8 |
The CVE-2023-44487 lined extensively above additionally applies to Chromium / Edge.
Appendix E: Finish of Servicing, Finish of Help, and different adjustments
These three tables cowl Microsoft merchandise altering standing on 10 October 2023.
| Finish of Servicing (2 merchandise) |
| Dynamics 365 Enterprise Central on-premises (Fashionable Coverage), 2022 launch wave 1, model 20.x |
| Home windows 11 Dwelling and Professional, Model 21H2 |
| Finish of Help (21 merchandise) |
| Excel 2019 for Mac |
| Hyper-V Server 2012 |
| Hyper-V Server 2012 R2 |
| Web Explorer 7 |
| Web Data Providers (IIS), IIS 8 on Home windows Server 2012 |
| Web Data Providers (IIS), IIS 8.5 on Home windows Server 2012 R2 |
| Microsoft Workplace 2019 for Mac |
| Microsoft Workplace Audit and Management Administration Server 2013 |
| Outlook 2019 for Mac |
| PowerPoint 2019 for Mac |
| Home windows Embedded Compact 2013 |
| Home windows Embedded POSReady 7, Prolonged Safety Replace 12 months 2* |
| Home windows Embedded Commonplace 7, Prolonged Safety Replace 12 months 3* |
| Home windows MultiPoint Server 2012 |
| Home windows Server 2012 |
| Home windows Server 2012 R2 |
| Home windows Server Replace Providers for Home windows Server 2012 |
| Home windows Server Replace Providers for Home windows Server 2012 R2 |
| Home windows Storage Server 2012 |
| Home windows Storage Server 2012 R2 |
| Phrase 2019 for Mac |
| Transferring from Mainstream to Prolonged Help (11 merchandise) |
| Entry 2019 |
| Dynamics 365 Enterprise Central on-premises (Mounted Coverage) |
| Excel 2019 |
| Microsoft Workplace 2019 |
| OneNote 2016 |
| Outlook 2019 |
| PowerPoint 2019 |
| Venture 2019 |
| Writer 2019 |
| Visio 2019 |
| Phrase 2019 |
[ad_2]