[ad_1]
In August 2023, the Sophos X-Ops Incident Response staff was engaged to assist a company in Australia contaminated with Cash Message ransomware. This assault vector, identified for its stealth, doesn’t append any file extensions to the encrypted knowledge, making it tougher for victims to determine the encrypted information just by recognizing such extensions.
On this submit, we’ll have a look at the incident assault stream, illustrating how risk actors are deploying the Cash Message ransomware and what measures can fight attacker efforts at varied factors alongside the MITRE ATT&CK chain.
Make an observation of it
As a part of its routine, the ransomware drops a ransom word named “money_message.log” immediately into the basis listing of the C: drive.
The ransom word on the goal’s system learn as follows:
Your information was encrypted by “Cash message” worthwhile group and may’t be accessed anymore.
In case you pay ransom, you’re going to get a decryptor to decrypt them. Don’t attempt to decrypt information your self – in that case they are going to be broken and unrecoverable.
For additional negotiations open this <redacted>.onion/<redacted>
utilizing tor browser https://www.torproject.org/obtain/
In case you refuse to pay, we’ll submit the information we stole out of your inner community, in our weblog:
<redacted>.onion
Encrypted information can’t be decrypted with out our decryption software program.
<redacted>.onion/<redacted>
Assault Circulation Particulars
Preliminary Entry
Our investigation signifies that the attacker gained preliminary entry by way of the goal’s VPN, which was utilizing single-factor authentication. That is an instance of MITRE’s T1078 – Legitimate Accounts method.
Steerage
Implementing multifactor authentication (MFA) for VPN connections is paramount to reinforce safety and thwart potential unauthorized entry. Moreover, steady monitoring of VPN logs and consumer exercise must be in place to promptly detect any suspicious login makes an attempt or anomalies. Upgrading to a extra sturdy and layered authentication strategy, similar to MFA, is crucial to bolster the primary line of protection in opposition to potential risk actors in search of to take advantage of single-factor vulnerabilities and acquire unauthorized VPN entry.
Protection Evasion
The risk actor deployed GPO Coverage to disable Home windows Defender real-time safety. That is an instance of MITRE’s T1562.001: Impair Defenses: Disable or Modify Instruments sub-technique.
[HKEY_LOCAL_MACHINESoftwarePoliciesMicrosoftWindows Defender] DisableAntiSpyware: [REG_DWORD_LE] 1 [HKEY_LOCAL_MACHINESoftwarePoliciesMicrosoftWindows DefenderReal-time Protection] DisableRealtimeMonitoring: [REG_DWORD_LE] 1
Steerage
The primary line of protection accessible to organizations is to make use of a safety agent that has sturdy tamper safety. By way of monitoring for this exercise, these are detection-ready occasion sources. Whereas it’s attainable a system administrator would disable these protections (no less than briefly) throughout troubleshooting, given the chance of this exercise, it’s one thing that must be investigated promptly if a corresponding assist ticket isn’t discovered.
Lateral Motion
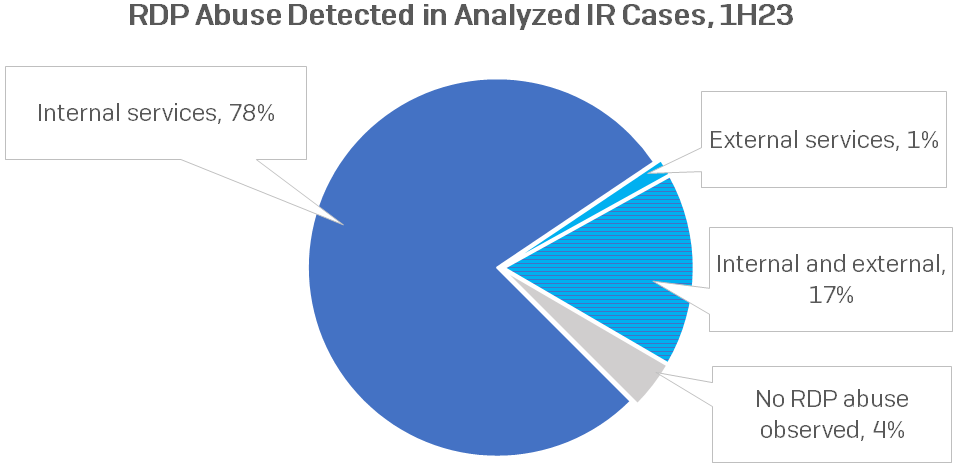
The risk actor leveraged psexec to run a batch script with the intention of enabling the RDP port, subsequently utilizing Distant Desktop Protocol (RDP) to traverse the community. That is an instance of MITRE’s T1021.001: Distant Providers: Distant Desktop Protocol sub-technique. RDP is a typical discovering in instances dealt with by Incident Response, as proven by our findings from IR instances dealt with throughout the first half of 2023.
Determine 1: RDP abuse detections in IR instances for the primary half of 2023
The batch script contents are as follows:
reg add "HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f Allow-NetFirewallRule -DisplayGroup 'Distant Desktop' netsh advfirewall firewall add rule title="Open Distant Desktop" protocol=TCP dir=in localport=3389 motion=permit
Steerage
Securing RDP entry will be troublesome for a lot of firms, however it’s a mission worthy of funding. The primary merchandise to test off the field is to limit, by position, which accounts can entry different programs utilizing RDP. The overwhelming majority of customers don’t want this entry. Secondly, adopting a centralized soar server, which solely admins can entry with MFA and blocking on the community stage different system-to-system RDP is a robust preventative management. Lastly, a detection must be in place to promptly evaluate anomalous RDP connections to deconflict them with accredited system administration exercise.
Credential Entry
The risk actor, utilizing Secretsdump.py (a part of the Impacket toolkit), retrieved the SAM registry hive. That is an instance of a method of executing MITRE’s T1003.002: OS Credential Dumping: Safety Account Supervisor subtechnique.
C:WINDOWSsystem32svchost.exe -k localService -p -s RemoteRegistry
Steerage
It’s essential for organizations to prioritize the safeguarding of delicate credentials. Implementing sturdy entry controls, using sturdy endpoint detection and response options, and monitoring for any suspicious exercise associated to SAM hive entry are important steps. Any unauthorized makes an attempt to entry or manipulate this essential system element must be promptly investigated, as they might point out a breach or malicious exercise that might compromise the safety of delicate credentials.
Assortment
A confirmed compromised account was used to entry delicate folders like Finance, Payroll, SalesReport and HR in FileServer. MITRE lists 37 sub- and sub-sub-techniques underneath TA0009: Assortment.
Steerage
Typically by the point a risk actor is staging knowledge, it’s too late to have a very good safety consequence. A great strategy to stop theft of knowledge is to undertake least-privilege entry, which implies making certain solely the required folks have entry, adopted by granular controls on exporting, sharing, or shifting the information. DLP options, whereas having a historical past of being troublesome to implement and keep, are price evaluating for high-risk knowledge.
Exfiltration
The risk actor leveraged MEGAsync to exfiltrate the information. That is an instance of MITRE’s T1567.002: Exfiltration Over Internet Service: Exfiltration to Cloud Storage.
UserAssist entry: 87 Worth title: C:Customers<redacted>AppDataLocalTemp6MEGAsyncSetup32.exe Depend: 1 Person ”<redacted> registered Activity Scheduler activity “MEGAMEGAsync Replace Activity S-1-5-21-<redacted>"
Steerage
Organizations ought to give attention to enhancing knowledge loss prevention measures and community monitoring. Implementing sturdy outbound site visitors evaluation and content material inspection might help determine and block suspicious knowledge transfers. Moreover, intently monitoring MEGAsync actions and detecting any uncommon or unauthorized knowledge transfers will be important in mitigating knowledge breaches. Quickly examine and reply to any indicators of unauthorized exfiltration to stop potential knowledge compromise and decrease the affect on knowledge confidentiality.
Impression
The risk actor leveraged two ransomware binaries, one for the Home windows atmosphere and one for the Linux atmosphere. The Home windows model is called home windows.exe, and is detected as Troj/Ransom-GWD by Sophos. That is an instance of MITRE’s T1486: Knowledge Encrypted for Impression.
- The Cash Message encryptor is written in C++ and contains an embedded JSON configuration file which accommodates some key particulars like what folders to dam from encrypting, what extension to append, what companies and processes to terminate, and area login names and passwords doubtless used to encrypt different gadgets.
- The encryptor makes use of the ChaCha Quarter Spherical algorithm and ECDH encryption
- The ransomware creates the C:money_message.log ransom word when full
- On endpoints protected with Sophos, the next detection is triggered:
Malware detected: ‘Troj/Ransom-GWD’ at ‘C:Customers<redacted>AppDataLocalTemp6windows.exe’
The Linux variant is called ‘esxi’, Upon execution it’ll delete all of the digital laborious disks. That is an instance of MITRE’s T1561: Disk Wipe.
Instructions executed on ESXi host:
cd /tmp/ chmod 777 esxi dir ls ./esxi
Steerage
As talked about earlier, at this late stage within the assault, having full protection on all programs with a correctly configured XDR answer is significant to guard organizations from ransomware. Within the case of Sophos, it’s essential for purchasers to have their CryptoGuard coverage activated, which is one thing assist can information clients on.
Conclusion
The Cash Message attackers’ path to exfiltration conforms to a reasonably typical MITRE ATT&CK chain, as we’ve proven above. Although this specific attacker tries to muddy the waters for defenders, good protection – particularly within the early levels – can present an efficient toolkit in opposition to unhealthy outcomes.
[ad_2]