[ad_1]
State-sponsored menace actors from the Democratic Folks’s Republic of Korea (DPRK) have been discovered concentrating on blockchain engineers of an unnamed crypto change platform by way of Discord with a novel macOS malware dubbed KANDYKORN.
Elastic Safety Labs stated the exercise, traced again to April 2023, reveals overlaps with the notorious adversarial collective Lazarus Group, citing an evaluation of the community infrastructure and methods used.
“Menace actors lured blockchain engineers with a Python utility to achieve preliminary entry to the setting,” safety researchers Ricardo Ungureanu, Seth Goodwin, and Andrew Pease stated in a report printed right now.
“This intrusion concerned a number of complicated levels that every employed deliberate protection evasion methods.”
This isn’t the primary time the Lazarus Group has leveraged macOS malware in its assaults. Earlier this yr, the menace actor was noticed distributing a backdoored PDF utility that culminated within the deployment of RustBucket, an AppleScript-based backdoor able to retrieving a second-stage payload from a distant server.
What makes the brand new marketing campaign stand out is the attacker’s impersonation of blockchain engineers on a public Discord server, using social engineering lures to trick victims into downloading and executing a ZIP archive containing malicious code.
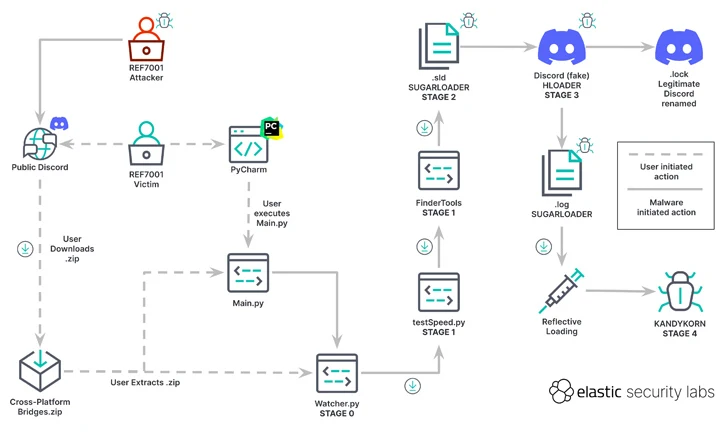
“The sufferer believed they had been putting in an arbitrage bot, a software program device able to cashing in on cryptocurrency fee variations between platforms,” the researchers stated. However in actuality, the assault chain paved the best way for the supply of KANDYKORN following a five-stage course of.
“KANDYKORN is a sophisticated implant with quite a lot of capabilities to observe, work together with, and keep away from detection,” the researchers stated. “It makes use of reflective loading, a direct-memory type of execution that will bypass detections.”
The start line is a Python script (watcher.py), which retrieves one other Python script (testSpeed.py) hosted on Google Drive. This dropper, for its half, fetches another Python file from a Google Drive URL, named FinderTools.
FinderTools additionally capabilities as a dropper, downloading and executing a hidden second stage payload known as SUGARLOADER (/Customers/shared/.sld and .log) that finally connects to a distant server with the intention to retrieve KANDYKORN and execute it immediately in reminiscence.
SUGARLOADER can be liable for launching a Swift-based self-signed binary generally known as HLOADER that makes an attempt to go off because the professional Discord utility and executes .log (i.e., SUGARLOADER) to attain persistence utilizing a way referred to as execution circulate hijacking.
KANDYKORN, which is the final-stage payload, is a full-featured reminiscence resident RAT with built-in capabilities to enumerate information, run extra malware, exfiltrate knowledge, terminate processes, and run arbitrary instructions.
“The DPRK, by way of models just like the LAZARUS GROUP, continues to focus on crypto-industry companies with the aim of stealing cryptocurrency with the intention to circumvent worldwide sanctions that hinder the expansion of their financial system and ambitions,” the researchers stated.
Kimsuky Resurfaces with Up to date FastViewer Malware
The disclosure comes because the S2W Menace Evaluation workforce uncovered an up to date variant of an Android spyware and adware referred to as FastViewer that is utilized by a North Korean menace cluster dubbed Kimsuky (aka APT43), a sister hacking outfit of the Lazarus Group.
FastViewer, first documented by the South Korean cybersecurity agency in October 2022, abuses Android’s accessibility providers to covertly harvest delicate knowledge from compromised units by masquerading itself as seemingly innocent safety or e-commerce apps which can be propagating by way of phishing or smishing.
It is also designed to obtain a second-stage malware named FastSpy, which is predicated on the open-source venture AndroSpy, to execute knowledge gathering and exfiltration instructions.
“The variant has been in manufacturing since at the very least July 2023 and, just like the preliminary model, is discovered to induce set up by distributing repackaged APKs that embody malicious code in professional apps,” S2W stated.
One notable facet of the brand new model is the combination of FastSpy’s performance into the FastViewer, thus obviating the necessity to obtain extra malware. That stated, S2W stated “there aren’t any recognized instances of this variant being distributed within the wild.”
[ad_2]