[ad_1]
The prolific risk actor often known as Scattered Spider has been noticed impersonating newly employed workers in focused corporations as a ploy to mix into regular on-hire processes and takeover accounts and breach organizations internationally.
Microsoft, which disclosed the actions of the financially motivated hacking crew, described the adversary as “probably the most harmful monetary prison teams,” calling out its operational fluidity and its capability to include SMS phishing, SIM swapping, and assist desk fraud into its assault mannequin.
“Octo Tempest is a financially motivated collective of native English-speaking risk actors identified for launching wide-ranging campaigns that prominently function adversary-in-the-middle (AiTM) strategies, social engineering, and SIM swapping capabilities,” the corporate mentioned.
It is value noting that the exercise represented by Octo Tempest is tracked by different cybersecurity corporations underneath varied monikers, together with 0ktapus, Scatter Swine, and UNC3944, which has repeatedly singled out Okta to acquire elevated permissions and infiltrate focused networks.
One of many key hallmarks is the concentrating on of assist and assist desk personnel through social engineering assaults to achieve preliminary entry to privileged accounts, tricking them into performing a reset of the sufferer’s password and multi-factor authentication (MFA) strategies.
Different approaches entail buying an worker’s credentials and/or session token(s) on a prison underground market, or calling the person straight and socially engineering the person to both set up a Distant Monitoring and Administration (RMM) utility, go to a faux login portal utilizing an AiTM phishing toolkit, or take away their FIDO2 token.
Preliminary assaults mounted by the group focused cell telecommunication suppliers and enterprise course of outsourcing (BPO) organizations to provoke SIM swaps, earlier than graduating to monetizing the entry for promoting SIM swaps to different criminals and performing account takeovers of high-net-worth people for cryptocurrency theft.
Octo Tempest has since diversified its concentrating on to incorporate electronic mail and tech service suppliers, gaming, hospitality, retail, managed service suppliers (MSPs), manufacturing, know-how, and monetary sectors, whereas concurrently rising as an affiliate for the BlackCat ransomware gang in mid-2023 to extort victims.
Put in another way, the tip objective of the assaults differ between cryptocurrency theft and information exfiltration for extortion and ransomware deployment.
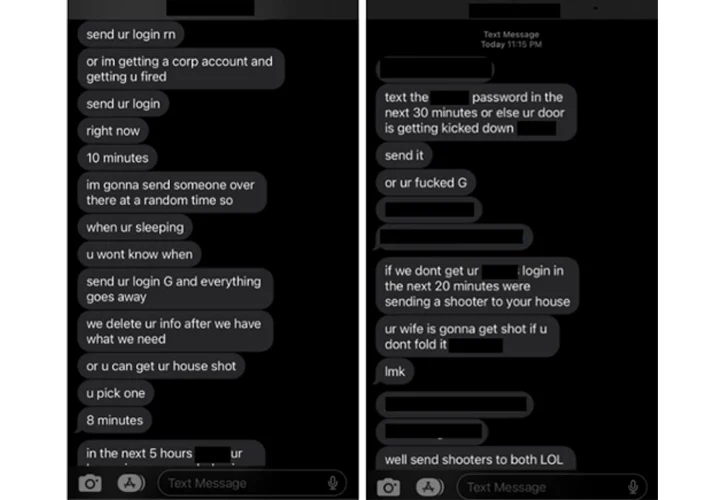
“In late 2022 to early 2023, […] Octo Tempest began monetizing intrusions by extorting sufferer organizations for information stolen throughout their intrusion operations and in some circumstances even resorting to bodily threats,” Microsoft mentioned.
“In uncommon cases, Octo Tempest resorts to fear-mongering techniques, concentrating on particular people by way of cellphone calls and texts. These actors use private info, similar to residence addresses and household names, together with bodily threats to coerce victims into sharing credentials for company entry.”
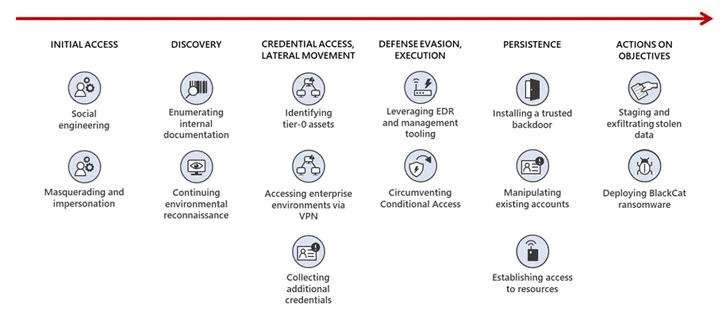
A profitable foothold is adopted by the attackers finishing up reconnaissance of the atmosphere and privilege escalation, the latter of which is completed by way of stolen password coverage procedures, bulk downloads of person, group, and position exports.
One other noteworthy tradecraft is use of compromised safety personnel accounts inside sufferer organizations to impair the functioning safety merchandise in an try to fly underneath the radar, along with tampering with the safety workers mailbox guidelines to mechanically delete emails from distributors.
The broad arsenal of instruments and techniques employed by Octo Tempest, together with enrolling actor-controlled gadgets into system administration software program to bypass controls and replaying harvested tokens with glad MFA claims to bypass MFA, is indicative of its in depth technical experience and its capability to navigate complicated hybrid environments, Redmond mentioned.
“A novel approach Octo Tempest makes use of is compromising VMware ESXi infrastructure, putting in the open-source Linux backdoor Bedevil, after which launching VMware Python scripts to run arbitrary instructions towards housed digital machines,” the corporate additional defined.
[ad_2]