[ad_1]
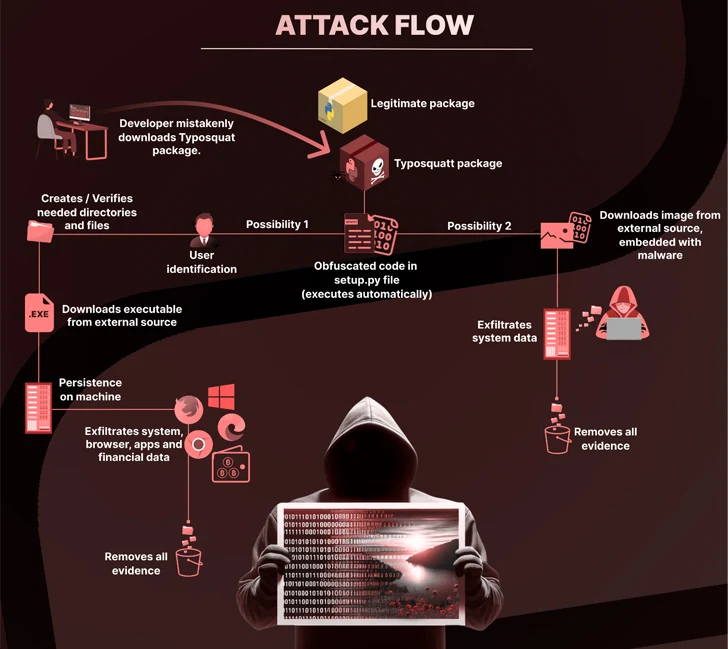
An unknown risk actor has been noticed publishing typosquat packages to the Python Package deal Index (PyPI) repository for almost six months with an intention to ship malware able to gaining persistence, stealing delicate information, and accessing cryptocurrency wallets for monetary achieve.
The 27 packages, which masqueraded as widespread official Python libraries, attracted hundreds of downloads, Checkmarx mentioned in a brand new report. A majority of the downloads originated from the U.S., China, France, Hong Kong, Germany, Russia, Eire, Singapore, the U.Ok., and Japan.
“A defining attribute of this assault was the utilization of steganography to cover a malicious payload inside an innocent-looking picture file, which elevated the stealthiness of the assault,” the software program provide chain safety agency mentioned.
Among the packages are pyefflorer, pyminor, pyowler, pystallerer, pystob, and pywool, the final of which was planted on Might 13, 2023.
A standard denominator to those packages is using the setup.py script to incorporate references to different malicious packages (i.e., pystob and pywool) that deploy a Visible Primary Script (VBScript) as a way to obtain and execute a file named “Runtime.exe” to realize persistence on the host.
Embedded inside the binary is a compiled file that is able to gathering data from internet browsers, cryptocurrency wallets, and different purposes.
An alternate assault chain noticed by Checkmarx is alleged to have hidden the executable code inside a PNG picture (“uwu.png”), which is subsequently decoded and run to extract the general public IP handle and the universally distinctive identifier (UUID) of the affected system.
Pystob and Pywool, particularly, have been printed beneath the guise of instruments for API administration, solely to exfiltrate the info to a Discord webhook and try to keep up persistence by inserting the VBS file within the Home windows startup folder.
“This marketing campaign serves as one other stark reminder of the ever-present threats that exist in immediately’s digital panorama, significantly in areas the place collaboration and open alternate of code are foundational,” Checkmarx mentioned.
The event comes as ReversingLabs uncovered a brand new wave of protestware npm packages that “conceal scripts broadcasting messages of peace associated to the conflicts in Ukraine and in Israel and the Gaza Strip.”
One of many packages, named @snyk/sweater-comb (model 2.1.1), determines the geographic location of the host, and if it is discovered to be Russia, shows a message criticizing the “unjustified invasion” of Ukraine by one other module referred to as “es5-ext.”
One other package deal, e2eakarev, has the outline “free palestine protest package deal” within the package deal.json file, and carries out comparable checks to see if the IP handle resolves to Israel, and in that case, log what’s described as a “innocent protest message” that urges builders to boost consciousness in regards to the Palestinian battle.
It isn’t simply risk actors infiltrating open-source ecosystems. Earlier this week, GitGuardian revealed the presence of three,938 complete distinctive secrets and techniques throughout 2,922 PyPI tasks, of which 768 distinctive secrets and techniques have been discovered to be legitimate.
This contains AWS keys, Azure Lively Listing API keys, GitHub OAuth app keys, Dropbox keys, SSH keys, and credentials related to MongoDB, MySQL, PostgreSQL, Coinbase, and Twilio.
What’s extra, many of those secrets and techniques have been leaked greater than as soon as, spanning a number of launch variations, bringing the entire variety of occurrences to 56,866.
“Exposing secrets and techniques in open-source packages carries important dangers for builders and customers alike,” GitGuardian’s Tom Forbes mentioned. “Attackers can exploit this data to realize unauthorized entry, impersonate package deal maintainers, or manipulate customers by social engineering ways.”
The continual wave of assaults focusing on the software program provide chain has additionally prompted the U.S. authorities to difficulty new steering this month for software program builders and suppliers to keep up and supply consciousness about software program safety.
“It is suggested that acquisition organizations assign provide chain threat assessments to their shopping for choices given the latest excessive profile software program provide chain incidents,” the Cybersecurity and Infrastructure Safety Company (CISA), Nationwide Safety Company (NSA), and the Workplace of the Director of Nationwide Intelligence (ODNI) mentioned.
“Software program builders and suppliers ought to enhance their software program growth processes and scale back the chance of hurt to not simply workers and shareholders, but in addition to their customers.”
[ad_2]