
[ad_1]
We’re excited to announce the final availability (GA) of a number of key safety features for Databricks on Google Cloud:
- Personal connectivity with Personal Service Join (PSC)
- Buyer-managed encryption keys
- IP entry lists for Account console and API entry
At Databricks, we acknowledge that knowledge is your most useful asset. With the GA of those crucial safety capabilities, you possibly can shield your knowledge at relaxation, hold your knowledge non-public, and mitigate knowledge exfiltration dangers on the Databricks Lakehouse Platform.
On this weblog, we are going to deal with generally requested safety questions and stroll you thru the brand new safety features and capabilities that are actually typically accessible on Google Cloud.
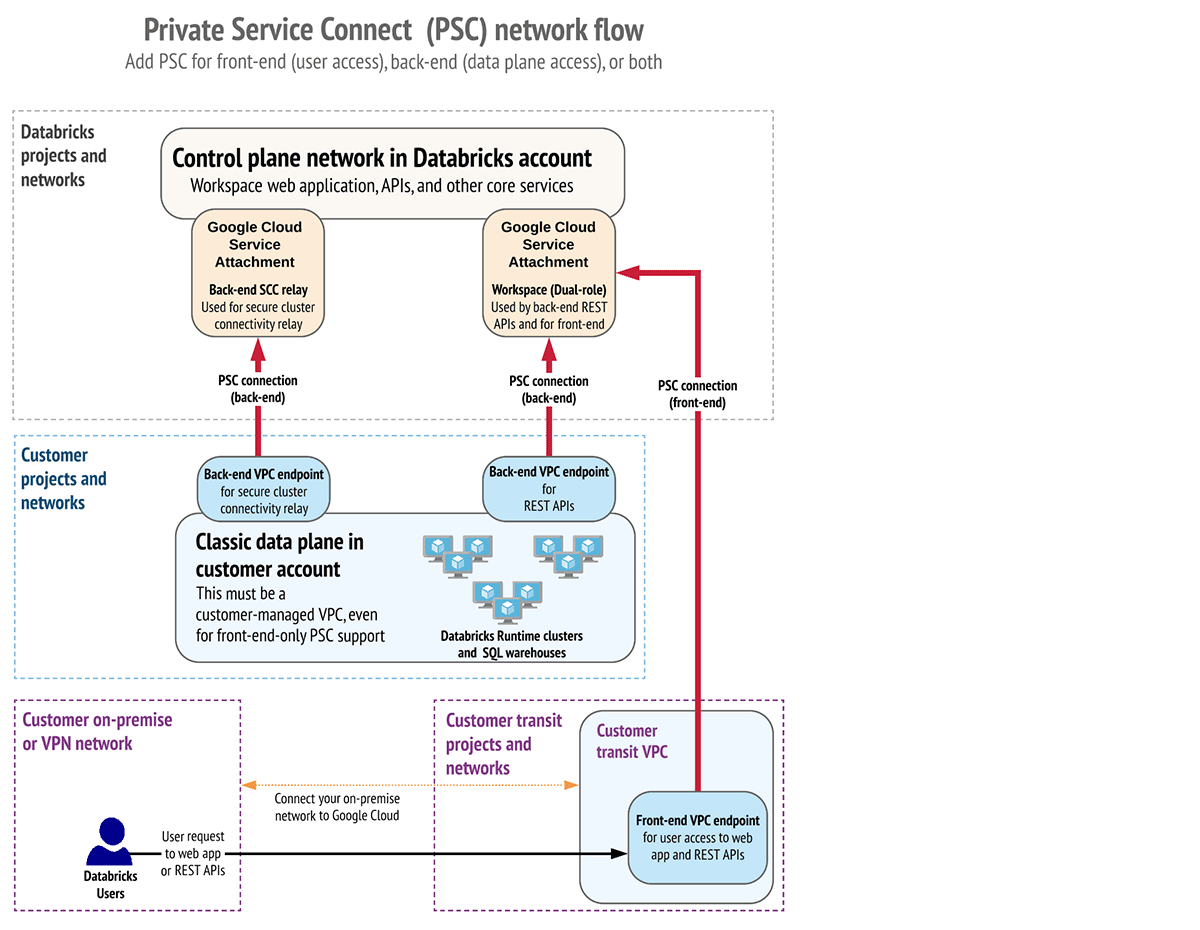
Finish-to-end non-public workspaces with Personal Service Join
Most enterprise prospects wish to be sure that their customers and workloads can course of their safety knowledge in a non-public and remoted atmosphere. With Databricks, you possibly can safe the community perimeter and configure end-to-end non-public connectivity with the customer-managed digital non-public cloud (VPC) and Personal Service Join (PSC). This consists of:
- The power to privately connect with the Databricks net software and APIs from a consumer. Databricks supplies the power to restrict entry to a Workspace to solely licensed VPC endpoints and public IP addresses.
- The power to privately connect with the Databricks compute assets in a customer-managed VPC (the information aircraft) to the Databricks workspace core companies (the management aircraft).
Now in Restricted Availability with GA-level performance, Personal Service Join can now be leveraged by Google Cloud prospects for his or her Databricks workspaces with the advice for manufacturing use, full assist, and SLAs. A PSC-enabled non-public workspace helps you mitigate a number of knowledge exfiltration dangers, resembling entry from unauthorized networks utilizing leaked credentials or publicity of information on the web.
Our latest Databricks on Google Cloud Safety Finest Practices weblog explains how one can isolate your Databricks atmosphere and safe your knowledge utilizing capabilities resembling customer-managed VPCs, Personal Service Join and IP ACLs.
Defend your knowledge at relaxation with customer-managed keys
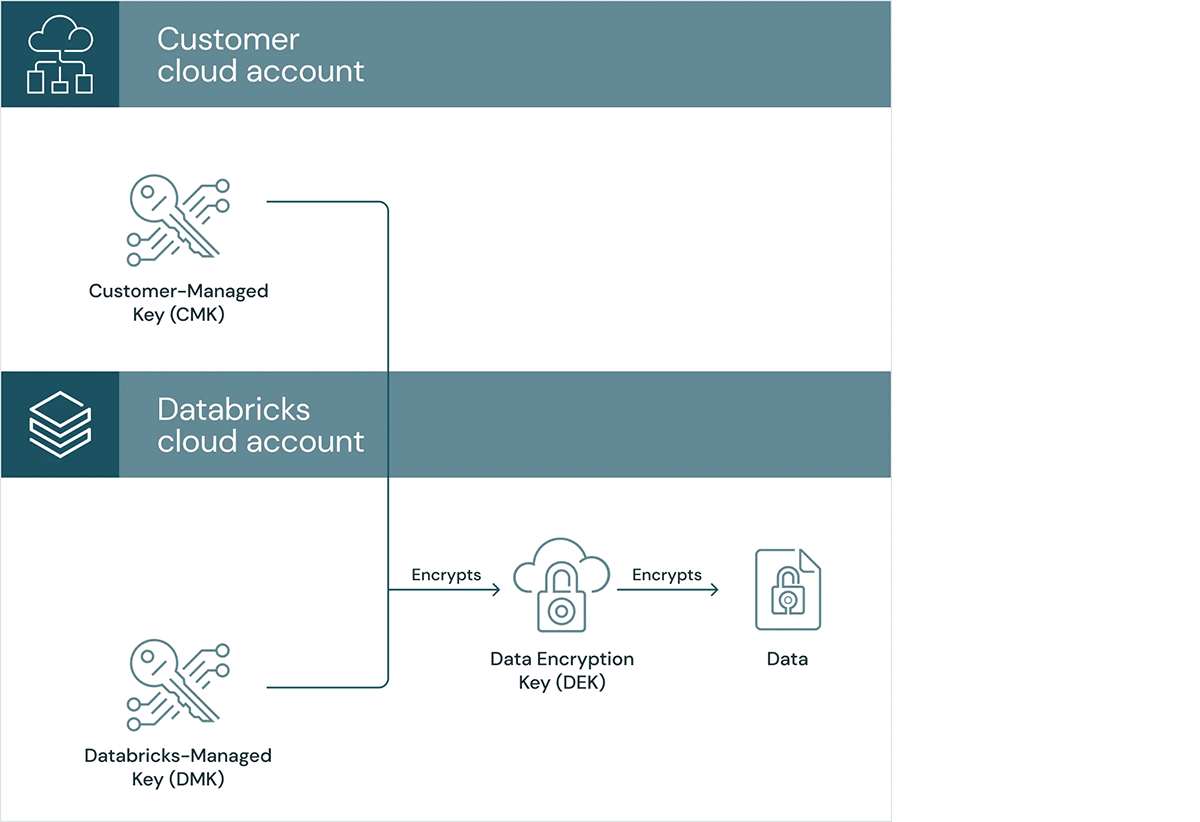
Databricks encrypts all knowledge at relaxation by default inside our managed companies. For added management and visibility, a number of enterprise prospects additionally want the power to guard their knowledge with encryption keys managed by them in Cloud KMS.
Now typically accessible on Google Cloud, Databricks customer-managed keys for encryption function lets you convey your personal encryption keys to guard knowledge at relaxation in Databricks managed companies and workspace storage:
- Buyer-managed keys for managed companies: Managed companies knowledge within the Databricks management aircraft is encrypted at relaxation. You’ll be able to add a customer-managed key for managed companies to assist shield and management entry to the next sorts of encrypted knowledge:
- Pocket book supply recordsdata which can be saved within the management aircraft
- Pocket book outcomes for notebooks which can be saved within the management aircraft
- Secrets and techniques saved by the key supervisor APIs
- Databricks SQL queries and question historical past
- Private entry tokens or different credentials used to arrange Git integration with Databricks Repos
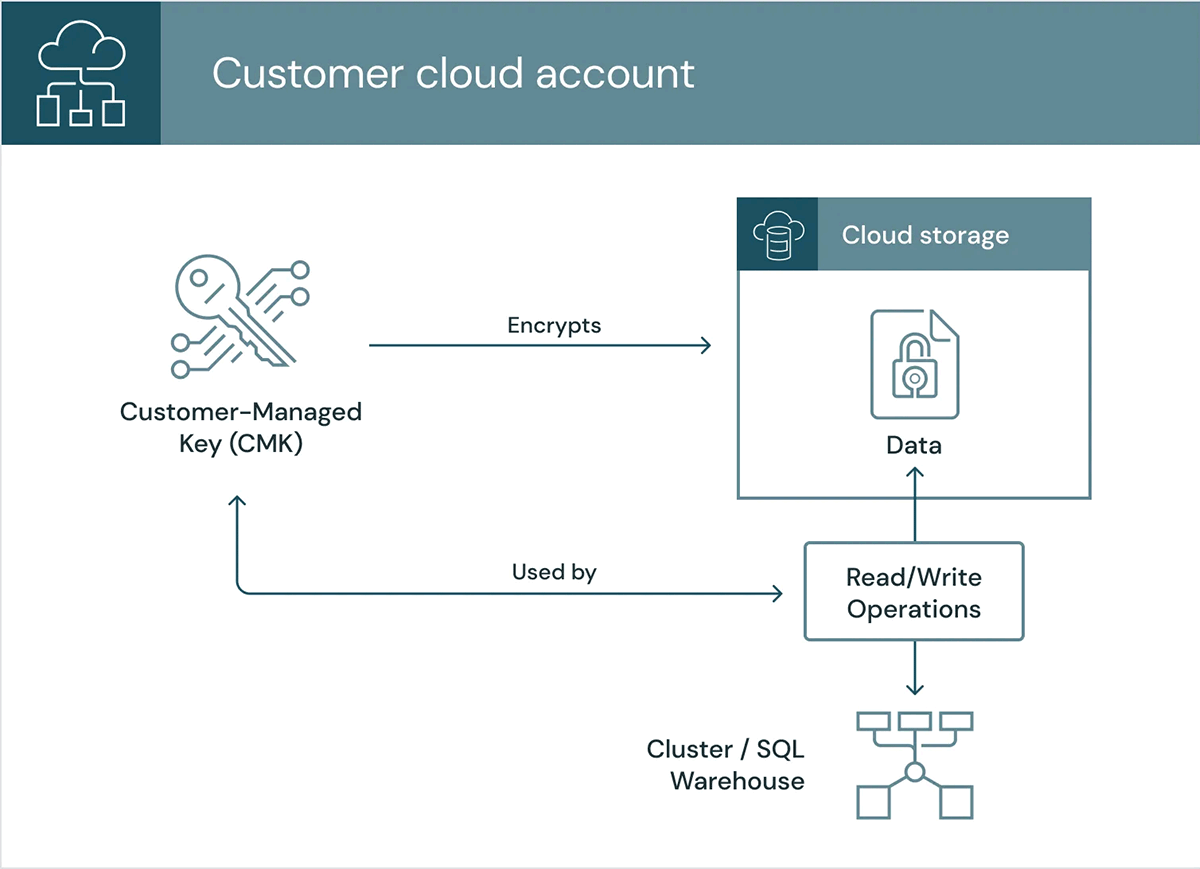
- Buyer-managed keys for workspace storage: Databricks additionally helps configuring customer-managed keys for workspace storage to assist shield and management entry to knowledge. You’ll be able to configure your personal key to encrypt the information on the GCS bucket related to the Google Cloud mission that you simply specified while you created your workspace. The identical key can be used to encrypt your cluster’s GCE persistent disks.
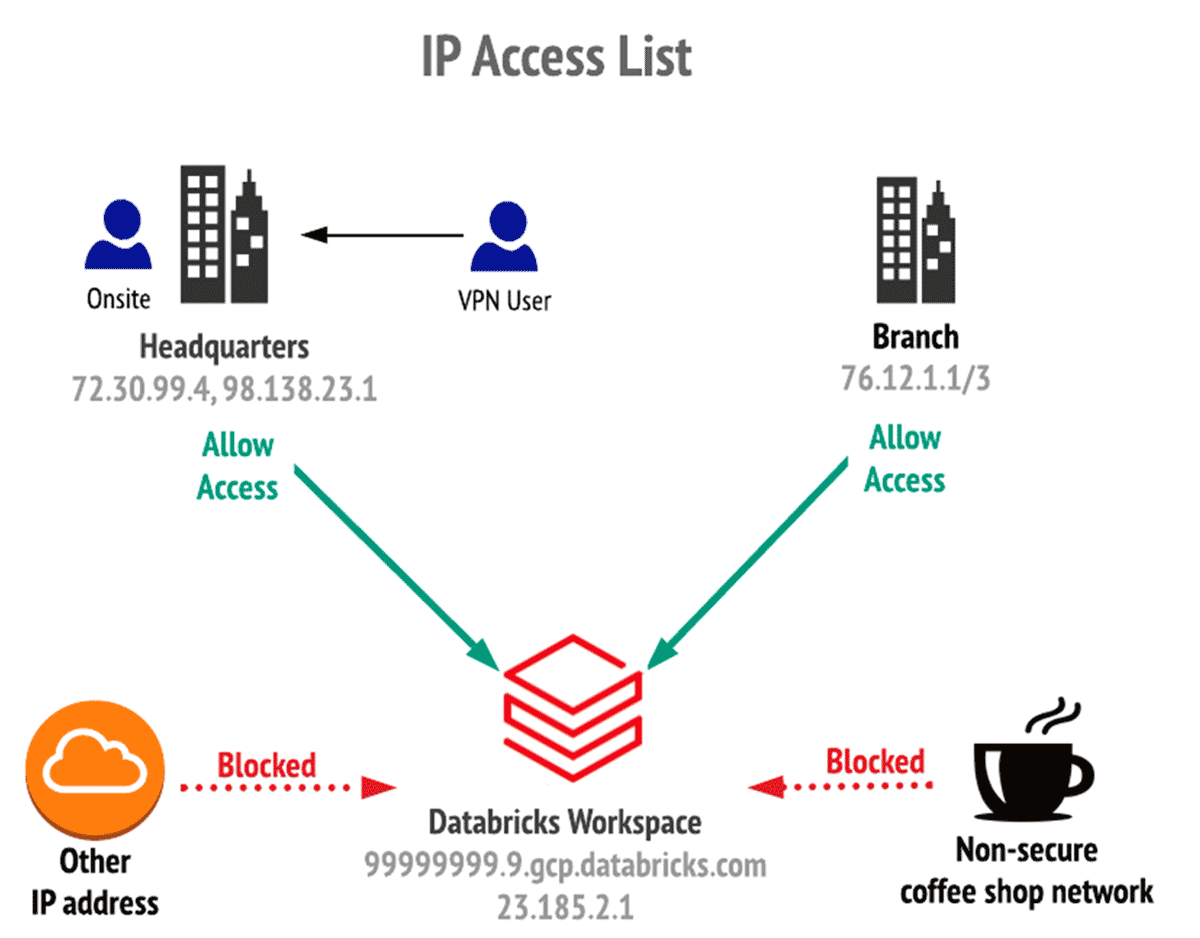
Safe your community perimeter with IP entry lists
IP entry lists (IP ACLs) let you management the networks permitted to entry your Databricks assets over the web. IP ACLs aid you cut back the chance of unauthorized entry utilizing stolen credentials and meet compliance necessities. For instance, particular industries and regulatory frameworks require organizations to limit entry to knowledge or purposes based mostly on geographical places or particular IPs.
There are two sorts of IP ACLs on Databricks now typically accessible on Google Cloud:
- IP entry lists for workspaces let you configure Databricks workspaces in order that customers and shoppers solely connect with the service from accepted company networks or a set of accepted IP addresses.
- IP entry lists for the account console enable account house owners and accounts admin to hook up with the account console UI and account-level REST APIs, such because the Account API solely by means of current company networks with a safe perimeter and a set of accepted IP addresses. Account house owners and admins can use an account console UI or a REST API to configure allowed and blocked IP addresses and subnets
Getting Began with Personal Service Join, CMK, and IP ACLs on Databricks on Google Cloud
Personal Service Join, customer-managed keys, and IP ACLs can be found on the Premium Tier of Google Cloud. For step-by-step directions on configuring these options on your Databricks workspaces, consult with our documentation (Personal Service Join | CMK | IP ACLs). Please observe that Databricks assist for personal connectivity utilizing Personal Service Join (PSC) is in Restricted Availability, with GA-level performance. Contact your Databricks consultant to request entry.
Please go to our Safety and Belief Middle for extra details about Databricks safety practices and options accessible to prospects.
[ad_2]