
[ad_1]
The Federal Bureau of Investigation and Cybersecurity & Infrastructure Safety Company warned in a joint advisory a few menace actor deploying a botnet that makes use of the Androxgh0st malware. This malware is able to gathering cloud credentials, similar to these from AWS or Microsoft Azure and extra, abusing the Easy Mail Switch Protocol, and scanning for Amazon Easy E-mail Service parameters.
What’s the Androxgh0st malware?
The Androxgh0st malware was uncovered in December 2022 by Lacework, a cloud safety firm. The malware is written in Python and is primarily used to steal Laravel.env recordsdata, which comprise secrets and techniques similar to credentials for high-profile functions. As an illustration, organizations can combine functions and platforms similar to AWS, Microsoft Workplace 365, SendGrid or Twilio to the Laravel framework, with all the functions’ secrets and techniques being saved within the .env file.
The botnet hunts for web sites utilizing the Laravel internet utility framework earlier than figuring out if the area’s root degree .env file is uncovered and incorporates information for accessing extra providers. The information within the .env file is perhaps usernames, passwords, tokens or different credentials.
The cybersecurity firm Fortinet uncovered telemetry on Androxgh0st, which reveals greater than 40,000 gadgets contaminated by the botnet (Determine A).
Determine A
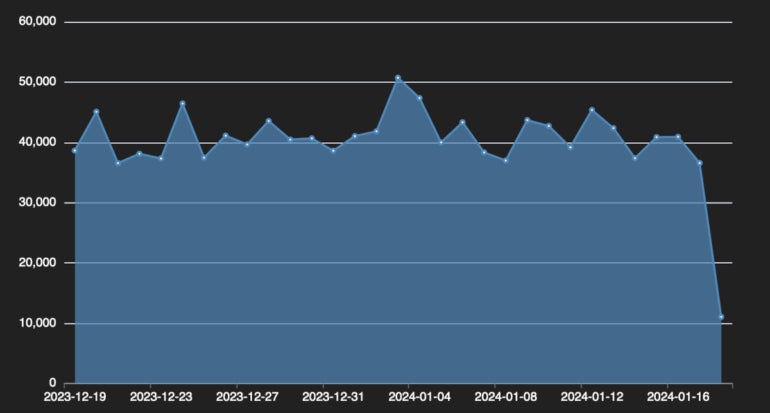
The FBI/CISA advisory states: “Androxgh0st malware additionally helps quite a few capabilities able to abusing the Easy Mail Switch Protocol (SMTP), similar to scanning and exploiting uncovered credentials and utility programming interfaces (APIs), and internet shell deployment.”
How can Androxgh0st malware exploit outdated vulnerabilities?
As well as, Androxgh0st can entry the Laravel utility key; if that secret is uncovered and accessible, the attackers will attempt to use it to encrypt PHP code that’s handed to the web site as a worth for the XSRF-TOKEN variable. That is an try to take advantage of the CVE-2018-15133 vulnerability in some variations of the Laravel internet utility framework. A profitable try permits the attacker to remotely add recordsdata to the web site. CISA added the CVE-2018-15133 Laravel deserialization of untrusted information vulnerability to its Identified Exploited Vulnerabilities Catalog primarily based on this proof of lively exploitation.
The menace actor deploying Androxgh0st has additionally been noticed exploiting CVE-2017-9841, a vulnerability within the PHP Testing Framework PHPUnit that enables an attacker to execute distant code on the web site.
CVE-2021-41773 can also be exploited by the menace actor. This vulnerability in Apache HTTP Server permits an attacker to execute distant code on the web site.
What is thought about Androxgh0st malware’s spamming goal?
Lacework wrote in late 2022 that “over the previous 12 months, practically a 3rd of compromised key incidents noticed by Lacework are believed to be for the needs of spamming or malicious electronic mail campaigns,” with nearly all of the exercise being generated by Androxgh0st.
The malware has a number of options to allow SMTP abuse, together with scanning for Amazon’s Easy E-mail Service sending quotas, in all probability for future spamming utilization.
The way to defend from this Androxgh0st malware menace
The joint advisory from CISA and the FBI recommends taking the next actions:
- Maintain all working techniques, software program and firmware updated. Particularly, Apache servers have to be updated. As might be learn on this article, attackers are nonetheless in a position to set off an Apache Internet server vulnerability that was patched in 2021.
- Confirm that the default configuration for all URIs is to disclaim entry until there’s a particular want for it to be accessible from the web.
- Guarantee Laravel functions will not be configured to run in debug or testing mode as a result of it would permit attackers to take advantage of weaknesses extra simply.
- Take away all cloud credentials from .env recordsdata and revoke them. As said by CISA and the FBI, “all cloud suppliers have safer methods to supply non permanent, steadily rotated credentials to code operating inside an internet server with out storing them in any file.”
- Evaluate any platforms or providers that use .env recordsdata for unauthorized entry or use.
- Seek for unknown or unrecognized PHP recordsdata, particularly within the root folder of the online server and within the /vendor/phpunit/phpunit/src/Util/PHP folder if PHPUnit is being utilized by the online server.
- Evaluate outgoing GET requests to file internet hosting platforms (e.g., GitHub and Pastebin), notably when the request accesses a .php file.
As well as, it’s suggested to test for any newly created person for any of the affected providers, as a result of Androxgh0st has been noticed creating new AWS cases used for added scanning actions.
Safety options have to be deployed on all endpoints and servers from the group to detect any suspicious exercise. When potential, your IT division ought to deploy multifactor authentication on all providers the place potential to keep away from being compromised by an attacker in possession of legitimate credentials.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.
[ad_2]